Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
Advanced Penetration Testing by VP Techno Labs
$500.00$435.00VAPT covers only Find and Fix Vulnerabilities. But Penetration Testing covers not only Vulnerability fixing but also advanced Automatic and Manual SAST(Static Application Security Analysis) + DAST (Dynamic Application Security Analysis) along with The core part "How the Vulnerabilities can be used or exploited to gain advantage?"Advanced Penetration Testing by VP Techno Labs
VAPT covers only Find and Fix Vulnerabilities. But Penetration Testing covers not only Vulnerability fixing but also advanced Automatic and Manual SAST(Static Application Security Analysis) + DAST (Dynamic Application Security Analysis) along with The core part "How the Vulnerabilities can be used or exploited to gain advantage?" -
Cloud Penetration Testing
Protect your Cloud Environment with our best security solutions. As the demands of business innovation outstrip the capabilities of on-premises infrastructure, companies are turning to cloud solutions. Migrating to the cloud, on the other hand, brings with it new cybersecurity challenges. As you migrate to hybrid cloud systems, you must maintain visibility, control, and security. To keep ahead of new threats, you require effective cloud configuration at each important stage of your cloud transformation journey.Cloud Penetration Testing
Protect your Cloud Environment with our best security solutions. As the demands of business innovation outstrip the capabilities of on-premises infrastructure, companies are turning to cloud solutions. Migrating to the cloud, on the other hand, brings with it new cybersecurity challenges. As you migrate to hybrid cloud systems, you must maintain visibility, control, and security. To keep ahead of new threats, you require effective cloud configuration at each important stage of your cloud transformation journey. -
Cloud Security Assessments
$150.00A technical security assessment for cloud-deployed applications to assess for bad exposures, vulnerabilities, and deviations from the best practices. Cloud security assessments checks for vulnerabilities emerging from unintended network accessibility, misconfigurations, user accounts, and their permissions, access management, and so on.Cloud Security Assessments
A technical security assessment for cloud-deployed applications to assess for bad exposures, vulnerabilities, and deviations from the best practices. Cloud security assessments checks for vulnerabilities emerging from unintended network accessibility, misconfigurations, user accounts, and their permissions, access management, and so on. -
Compromise Assessment by SecurDefense
$4,500.00Compromise Assessment involves proactively searching for malware and attackers on your network which maybe present for sometime. They can silently exfiltrate data, listen patiently to confidential data or scan the network to get credentials strong enough to steal key information.Compromise Assessment by SecurDefense
Compromise Assessment involves proactively searching for malware and attackers on your network which maybe present for sometime. They can silently exfiltrate data, listen patiently to confidential data or scan the network to get credentials strong enough to steal key information. -
FourCore ATTACK – Breach and Attack Simulation
$3,000.00$2,000.00 / monthGet a true security validation with the FourCore ATTACK Breach and Attack Simulation Platform. We know that security controls are vast and complex, and there are always misconfigurations and gaps. Launch cyber-attack simulations and fix the security gaps in your infrastructure to ensure that you’re closing the loopholes that create vulnerabilities and in-roads for attackers.—onboard your critical assets within minutes onto our Cloud platform.FourCore ATTACK – Breach and Attack Simulation
Get a true security validation with the FourCore ATTACK Breach and Attack Simulation Platform. We know that security controls are vast and complex, and there are always misconfigurations and gaps. Launch cyber-attack simulations and fix the security gaps in your infrastructure to ensure that you’re closing the loopholes that create vulnerabilities and in-roads for attackers.—onboard your critical assets within minutes onto our Cloud platform.$2 000.00Was $3 000.00Save $1000 -
IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols.IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols. -
ISMAC Basic
$12.99$9.99 per endpoint/annumA versatile integrated SIEM that enables you to perform cybersecurity with an unified view.ISMAC Basic
A versatile integrated SIEM that enables you to perform cybersecurity with an unified view.$9.99Was $12.99Save $3 -
ISMAC SOAR
$29.99$25.99 / year with a 14-day free trial and a $6,000.00 sign-up feeFor large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.ISMAC SOAR
Category: Cloud Security Compliance Management Container Security Log Management Malware Detection and Analysis Security Incident Management and Response SOAR Threat Intelligence and Signature Feeds VAPT | SKU: 003For large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.$25.99Was $29.99Save $4 -
Kratikal Vulnerability Assessment & Penetration Testing Service
Kratikal, being a CERT-In Empanelled, provides a Vulnerability Assessment and Penetration Testing (VAPT) security service that focuses on discovering flaws in network, server, and system infrastructure. Organizational security is the emphasis of vulnerability assessment, whereas real-world exploitation is the objective of penetration testing.
Kratikal Vulnerability Assessment & Penetration Testing Service
Kratikal, being a CERT-In Empanelled, provides a Vulnerability Assessment and Penetration Testing (VAPT) security service that focuses on discovering flaws in network, server, and system infrastructure. Organizational security is the emphasis of vulnerability assessment, whereas real-world exploitation is the objective of penetration testing.
-
Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them.Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them. -
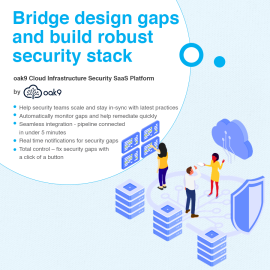
oak9 Cloud Infrastructure Security SaaS Platform
$2,000.00oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks.oak9 Cloud Infrastructure Security SaaS Platform
oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks. -
Red Team Assessment by Intelidata
Secure your applications against real-world vulnerabilities and run your business with confidence. Maximize security readiness by identifying real world vulnerabilities through rigorous intelligence driven security tests and replicating threat landscapes related to your business. Our Red Team exercises collate and analyze intelligent options which can be used by persistent attackers. We also test your existing security framework for any vulnerabilities to real time attacks.Red Team Assessment by Intelidata
Secure your applications against real-world vulnerabilities and run your business with confidence. Maximize security readiness by identifying real world vulnerabilities through rigorous intelligence driven security tests and replicating threat landscapes related to your business. Our Red Team exercises collate and analyze intelligent options which can be used by persistent attackers. We also test your existing security framework for any vulnerabilities to real time attacks. -
Red Team Assessments
$100.00Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization.Red Team Assessments
Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization. -
Red Teaming Assessment by VP Techno Labs
$600.00$550.00Red Teaming Assessment is ideal for medium to larger sized businesses. It is a combination of Social Engineering Testing, Vulnerability Assessment, Attack Simulation Testing and Assessment of Physical security. It uses prevention based approach. We uses some custom made tools along with some open source and commercial tools to cover maximum scope.Red Teaming Assessment by VP Techno Labs
Red Teaming Assessment is ideal for medium to larger sized businesses. It is a combination of Social Engineering Testing, Vulnerability Assessment, Attack Simulation Testing and Assessment of Physical security. It uses prevention based approach. We uses some custom made tools along with some open source and commercial tools to cover maximum scope. -
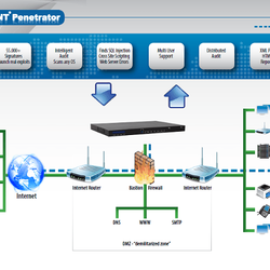
SecPoint Penetrator – VAPT
$250.00 – $12,750.00 / yearSecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.- Discover your weak points before it is too late.
- Ultimate Vulnerability Scanning
- Distributed Scanning Capability. Master / Client mode.
- Hardware 1U Rack or Virtual ESXi,Hyper-V,Linux Images
- Build in Ticket System
- Multiple Reporting: Consultant, Tech, Executive
- Multiple Report Formats: PDF, HTML & XML
- Not fixed on IP adresses, scan unlimited IPs, buy license for simultanous scan
SecPoint Penetrator – VAPT
SecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.- Discover your weak points before it is too late.
- Ultimate Vulnerability Scanning
- Distributed Scanning Capability. Master / Client mode.
- Hardware 1U Rack or Virtual ESXi,Hyper-V,Linux Images
- Build in Ticket System
- Multiple Reporting: Consultant, Tech, Executive
- Multiple Report Formats: PDF, HTML & XML
- Not fixed on IP adresses, scan unlimited IPs, buy license for simultanous scan
$250.00 – $12,750.00 / year -
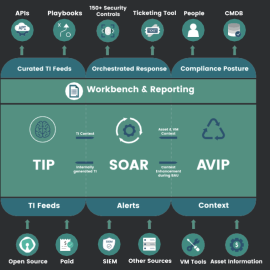
Securaa – Security Automation Platform
Securaa is a Comprehensive No Code Security Automation Platform that blends intelligence, risk-based asset management, vulnerability insights, automation and incident response into a single platform enabling SOC’s to reduce cybersecurity response time significantly and increase throughput manifolds.- Best RoI in the industry
- Reduce response time by over 95%
- Increase productivity by 300%
- Automate 100% L1 tasks
- Implement in weeks
- Build new playbook in hours
Securaa – Security Automation Platform
Securaa is a Comprehensive No Code Security Automation Platform that blends intelligence, risk-based asset management, vulnerability insights, automation and incident response into a single platform enabling SOC’s to reduce cybersecurity response time significantly and increase throughput manifolds.- Best RoI in the industry
- Reduce response time by over 95%
- Increase productivity by 300%
- Automate 100% L1 tasks
- Implement in weeks
- Build new playbook in hours