Description
Secure your applications against real-world vulnerabilities and run your business with confidence. Maximize security readiness by identifying real world vulnerabilities through rigorous intelligence driven security tests and replicating threat landscapes related to your business.
Our Red Team exercises collate and analyze intelligent options which can be used by persistent attackers. We also test your existing security framework for any vulnerabilities to real time attacks.
Our elite team of experts can assess your organization’s security effectiveness through a multilayered full scope attack simulation initiative designed to measure the readiness of your resources, networks, application, and physical security controls to overpower specific cyber threats.
Key business reasons to adopt Red Teaming services:
- Real time experience on how attacks happen
- Learn overview of potential strategies and methodologies of attackers
- Evaluate organizational capability to detect, respond and recover from threats
- Reach assessment reports with recommendations for your internal security teams
- Enhance Security, Improve Transparency, Strengthen Compliance
We provide you through visibility of various exploitative options which can be considered by attackers, including probable actions never imagined before. Our expertise identifies multiple fully cycle attack pathways and scenarios simultaneously while providing critical recommendations and observations. Your security staff’s ability to counter multiple attack front lines and safeguard assets will also be tested, our experts will observe their gaps and coach them to improve detect and response capabilities.
The purpose is to give you a transparent, unbiased external view of your organization’s security strengths, weaknesses and maturity to deal with cyber-attacks.
How we do it?
The objective of a red team test is to obtain a realistic idea of the level of risk and vulnerabilities against your technology, people and physical assets.
Technology – Networks, applications, routers, switches, appliances, etc.
People – Staff, independent contractors, departments, business partners, etc.
Physical Assets – Offices, warehouses, substations, data centers, buildings, etc.
Our Full Force Red Team Operations (red teaming) launches a multi-blended attack involving several facets of social engineering, physical penetration testing, application penetration testing and network penetration testing, simultaneously. It’s aimed at revealing real-world opportunities for malicious insiders or bad actors to be able to compromise all aspects of your organization in such a way that allows for unauthorized virtual and/or physical access to sensitive information leading up to data breaches and full system/network compromise.
Red team pen testing is an attack simulation carried out by our highly trained security consultants in an effort to:
- Identify physical, hardware, software and human vulnerabilities
- Obtain a more realistic understanding of risk for your organization
- Help address and fix all identified security weaknesses



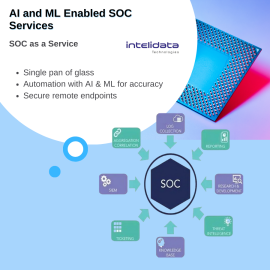

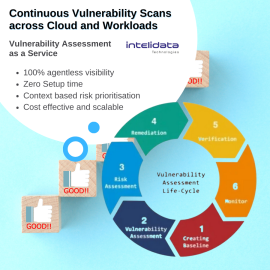



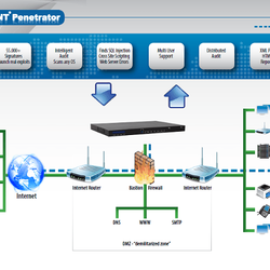




Description
Technical Experience
We are a qualified & highly technical team of Experienced Cyber Security Researchers, with cumulative experience of 25+ years. We partner with small to mid-sized companies to secure their businesses with easy step-by-step proven processes & Cert-in guidelines.
24/7 Services
We offer round-the-clock technical assistance. We never turn the cell phone off. It’s on 24/7 and it gets answered whenever you call, to give you timely deliveries. By outsourcing your IT security to us, you can focus on what you do best–running your business.
Flexible Pricing
No unexpected bills. No budget blow-outs. No missed deadlines. No broken promises. No shoddy service. No surprises. We believe in adding value to your business and provide meaningful service at a very cost efficient and budget -friendly pricing.
Training Assistance
We provide detailed steps & Cyber Security training to your Web Administrators and Developers for patching. No matter the budget, we pride ourselves on providing comprehensive professional assistance to them to secure your business.