Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
Accops HySecure: ZTNA-based Application Access Gateway
ZTNA-based Access Gateway to reduce attack surface even in a perimeter-less hybrid work environment.Accops HySecure: ZTNA-based Application Access Gateway
ZTNA-based Access Gateway to reduce attack surface even in a perimeter-less hybrid work environment. -
CyberQ Shield
CyberQ Shield is a Cloud Security & Compliance management solution that helps organizations using public cloud to automatically detect & respond to cloud security risks by following security best practices and comply with global security standards & benchmarks. CyberQ Shield is the leading 100% agentless security solution which can detect in “real time” both cloud IOC’s (Indicator of misconfiguration) and system vulnerabilities, it provides contextual security risk based on cloud environment, resources, data using unique labeling technique. Automated remediation using PLOP (Principle of least privilege) is one of the most advanced security capability within the platform.CyberQ Shield
CyberQ Shield is a Cloud Security & Compliance management solution that helps organizations using public cloud to automatically detect & respond to cloud security risks by following security best practices and comply with global security standards & benchmarks. CyberQ Shield is the leading 100% agentless security solution which can detect in “real time” both cloud IOC’s (Indicator of misconfiguration) and system vulnerabilities, it provides contextual security risk based on cloud environment, resources, data using unique labeling technique. Automated remediation using PLOP (Principle of least privilege) is one of the most advanced security capability within the platform. -
Desksight.ai
$30.00$29.00 for 1 year with a 2-week free trialDesksight.ai is a SaaS based Employee monitoring software product which collects and analyzes the data and provides insights to help organizations be more productive and compliant. DeskSight.ai is an Easy & quick set up experience. In other words, it’s Plug and Plays literally live in minutes with 4 simple steps:- Invite team members
- Install DeskSight agent
- Assign work definition
- Start monitoring
Desksight.ai
Desksight.ai is a SaaS based Employee monitoring software product which collects and analyzes the data and provides insights to help organizations be more productive and compliant. DeskSight.ai is an Easy & quick set up experience. In other words, it’s Plug and Plays literally live in minutes with 4 simple steps:- Invite team members
- Install DeskSight agent
- Assign work definition
- Start monitoring
$29.00Was $30.00Save $1 -
Impero Connect
$12.00 – $35.00 / yearImpero Connect (Formerly Netop Remote Access)- Remote Access for Retail, POS
- Remote Support and Secure Access for ATMs and Banks
- Remote Access for Production Technology
- Remote Control for BPO
- Remote Support for large organizations
- 256-bit AES encryption
- Centralized multi-factor authentication
- Multi-factor authentication through Microsoft Azure, RADIUS, RSA SecurID and Smartcards
- MAC or IP list-enabled machine access
- Complete logging with customizable audit trails and session recordings
- Exceeds PCI, GDPR, ISO & HIPAA compliance requirements for authentication & encryption
- Integration with Directory Services
- Access parameters for specific end users or devices
- Granular control over all user permissions through individual or group definitions
- Closed User Group license keys
- Customizable security roles
- Automatic locking or logging of remote machines in case of abnormal disconnection
- Restrict user access with application white-listing
Impero Connect
Impero Connect (Formerly Netop Remote Access)- Remote Access for Retail, POS
- Remote Support and Secure Access for ATMs and Banks
- Remote Access for Production Technology
- Remote Control for BPO
- Remote Support for large organizations
- 256-bit AES encryption
- Centralized multi-factor authentication
- Multi-factor authentication through Microsoft Azure, RADIUS, RSA SecurID and Smartcards
- MAC or IP list-enabled machine access
- Complete logging with customizable audit trails and session recordings
- Exceeds PCI, GDPR, ISO & HIPAA compliance requirements for authentication & encryption
- Integration with Directory Services
- Access parameters for specific end users or devices
- Granular control over all user permissions through individual or group definitions
- Closed User Group license keys
- Customizable security roles
- Automatic locking or logging of remote machines in case of abnormal disconnection
- Restrict user access with application white-listing
$12.00 – $35.00 / year -
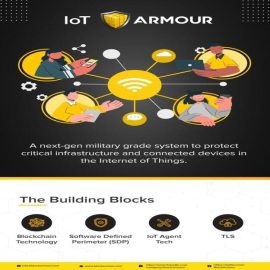
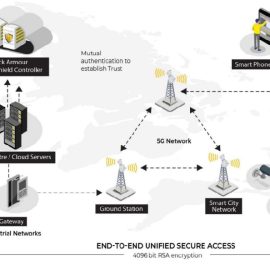
IoT Armour
With IoT Armour an organization can now move confidently into the journey of adopting IoT Sensors and Devices as part of their business processes. The solution utilizes a unique blockchain based digital identity for secure IOT device authentication and a policy based authorization to ensure only genuine devices and traffic is allowed to communicate with the IT based management systems. While reducing the attack surface available for attack by malware and ransomware.IoT Armour
With IoT Armour an organization can now move confidently into the journey of adopting IoT Sensors and Devices as part of their business processes. The solution utilizes a unique blockchain based digital identity for secure IOT device authentication and a policy based authorization to ensure only genuine devices and traffic is allowed to communicate with the IT based management systems. While reducing the attack surface available for attack by malware and ransomware. -
IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols.IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols. -
Network Configuration & Firewall Rules Review
$100.00Network architecture security review helps in identifying weaknesses & gaps of existing security controls and to comparing their alignment with the organization’s security objectives. Firewall Security audit checks for vulnerabilities, firewall configuration, and security policy.Network Configuration & Firewall Rules Review
Category: Network Access Control Network Behavior Analysis and Anomaly Detection Network Firewall (includes Next Generation Firewalls) Network Monitoring and Forensics |Network architecture security review helps in identifying weaknesses & gaps of existing security controls and to comparing their alignment with the organization’s security objectives. Firewall Security audit checks for vulnerabilities, firewall configuration, and security policy. -
Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them.Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them. -
Network Scanning and Hardening by Intelidata
Network Scanning is a method of getting network information such as identification of hosts, port information, and services by scanning networks and ports. Our Scanning Methodology includes the following steps: -- Checking for live systems
- Discovering open ports
- Scanning beyond IDS
- Banner grabbing
- Scanning Vulnerabilities
- Network Diagram Proxies and more
Network Scanning and Hardening by Intelidata
Network Scanning is a method of getting network information such as identification of hosts, port information, and services by scanning networks and ports. Our Scanning Methodology includes the following steps: -- Checking for live systems
- Discovering open ports
- Scanning beyond IDS
- Banner grabbing
- Scanning Vulnerabilities
- Network Diagram Proxies and more
-
ProDiscover
Platform for identification of look-alike mail domains. Proactive detection of look-alike domains through 14 types of domain variations.ProDiscover
Platform for identification of look-alike mail domains. Proactive detection of look-alike domains through 14 types of domain variations. -
Reblaze WAAP
About Reblaze: Reblaze provides a complete, cloud-based, comprehensive and proactive protection shield for web platforms (websites/web applications/API), together with a command and control system. We offer an all-in-one private virtual cloud-based solution (VPC) that includes IPS/WAF, DoS/DDoS protection, BOT detection and exclusion, anti-scraping, CDN and more. As a result of our unique approach, we monitor and cleanse the traffic before it reaches our customers' websites, and we can easily work with existing security solutions. The service requires a five-minute setup, zero installation, a single DNS change and can be deployed even under an attack. Service can be stopped at any stage and with a Try and Buy period of 30 days. We're fully integrated with AWS, GCP, and Azure, being able to build our platform in the clients' environment, ensuring privacy, enhancing the cloud's latency and efficiency, and also, reducing costs of traffic.Reblaze WAAP
About Reblaze: Reblaze provides a complete, cloud-based, comprehensive and proactive protection shield for web platforms (websites/web applications/API), together with a command and control system. We offer an all-in-one private virtual cloud-based solution (VPC) that includes IPS/WAF, DoS/DDoS protection, BOT detection and exclusion, anti-scraping, CDN and more. As a result of our unique approach, we monitor and cleanse the traffic before it reaches our customers' websites, and we can easily work with existing security solutions. The service requires a five-minute setup, zero installation, a single DNS change and can be deployed even under an attack. Service can be stopped at any stage and with a Try and Buy period of 30 days. We're fully integrated with AWS, GCP, and Azure, being able to build our platform in the clients' environment, ensuring privacy, enhancing the cloud's latency and efficiency, and also, reducing costs of traffic. -
SCRUTINY SENSOR
Scrutiny predicts the true nature of files by emulating the static and dynamic behavior in a crypto caged environment and simultaneously training self-learning sensors at the same time to provide accurate verdicts along with detailed analysis in seconds. Our unique approach detects both known and unknown ransomware strains without any reliance on data engrams, centralized signature databases, etc. Also, this stands out as multi-tier, more innovative, and advanced than the other ransomware detection methods available.SCRUTINY SENSOR
Category: Cloud Security Data Security Email Security Endpoint Security Industrial Security Internet of Things Security Malware Detection and Analysis |Scrutiny predicts the true nature of files by emulating the static and dynamic behavior in a crypto caged environment and simultaneously training self-learning sensors at the same time to provide accurate verdicts along with detailed analysis in seconds. Our unique approach detects both known and unknown ransomware strains without any reliance on data engrams, centralized signature databases, etc. Also, this stands out as multi-tier, more innovative, and advanced than the other ransomware detection methods available. -
Webroot DNS Protection
Stop up to 88% of malware at the domain layer by securing corporate and guest networks. Webroot® DNS Protection provides protective filtering for security, visibility, privacy and control. Minimize risks, maximize safety and productivity on the web. Webroot® DNS Protection is built for the future, supporting both IPv6 and DoH so businesses are prepared for the next generation of internet protocols and requests. This means you can protect your users at the DNS layer on modern networks like public hotspots without sacrificing security, privacy, visibility or admin control.Webroot DNS Protection
Stop up to 88% of malware at the domain layer by securing corporate and guest networks. Webroot® DNS Protection provides protective filtering for security, visibility, privacy and control. Minimize risks, maximize safety and productivity on the web. Webroot® DNS Protection is built for the future, supporting both IPv6 and DoH so businesses are prepared for the next generation of internet protocols and requests. This means you can protect your users at the DNS layer on modern networks like public hotspots without sacrificing security, privacy, visibility or admin control.