Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
Brand Protection by Foresiet
Continuous brand scan helps to protect from Impersonation, Phishing, Rogue website, Fake social media accounts, pages, mobile application etc.
Stay protected against counterfeiters and unauthorized replicas, while also being proactive in spotting and preventing phishing scams.
Brand Protection by Foresiet
Continuous brand scan helps to protect from Impersonation, Phishing, Rogue website, Fake social media accounts, pages, mobile application etc.
Stay protected against counterfeiters and unauthorized replicas, while also being proactive in spotting and preventing phishing scams.
-
D3 XGEN SOAR
Security Orchestration, Automation, and Response (SOAR) Platform
A nerve centre for security operations, incident response and threat hunting, XGEN SOAR orchestrates and automates workflows, helping each SOC tier, and enabling greater agility, visibility and confidence. Get the most from your security team and technology with a single SOAR solution for security automation, incident response, threat intelligence and case management.- Connected tools and teams
- Automate manual processes
- Uncover stealthy threats
- Speed, scale and strengthen
D3 XGEN SOAR
Security Orchestration, Automation, and Response (SOAR) Platform
A nerve centre for security operations, incident response and threat hunting, XGEN SOAR orchestrates and automates workflows, helping each SOC tier, and enabling greater agility, visibility and confidence. Get the most from your security team and technology with a single SOAR solution for security automation, incident response, threat intelligence and case management.- Connected tools and teams
- Automate manual processes
- Uncover stealthy threats
- Speed, scale and strengthen
-
DARKBEAST
DARKBEAST provides incident responders, threat hunters, investigators, and intelligence analyst with a robust technology to dive into the cybercrime underground and investigate through KELA’s dark web data lake. Gain Visibility into the underground operations and stay ahead of attackers, all while maintaining anonymity and abiding by any security restrictionsDARKBEAST
Category: Digital Risk Monitoring Specialized Threat Analysis and Protection Threat Intelligence and Signature Feeds |DARKBEAST provides incident responders, threat hunters, investigators, and intelligence analyst with a robust technology to dive into the cybercrime underground and investigate through KELA’s dark web data lake. Gain Visibility into the underground operations and stay ahead of attackers, all while maintaining anonymity and abiding by any security restrictions -
Desksight.ai
$30.00$29.00 for 1 year with a 2-week free trialDesksight.ai is a SaaS based Employee monitoring software product which collects and analyzes the data and provides insights to help organizations be more productive and compliant. DeskSight.ai is an Easy & quick set up experience. In other words, it’s Plug and Plays literally live in minutes with 4 simple steps:- Invite team members
- Install DeskSight agent
- Assign work definition
- Start monitoring
Desksight.ai
Desksight.ai is a SaaS based Employee monitoring software product which collects and analyzes the data and provides insights to help organizations be more productive and compliant. DeskSight.ai is an Easy & quick set up experience. In other words, it’s Plug and Plays literally live in minutes with 4 simple steps:- Invite team members
- Install DeskSight agent
- Assign work definition
- Start monitoring
$29.00Was $30.00Save $1 -
Digital Risk Protection by Foresiet
Digital risk score is a new way to measure the risk of digital assets, and it is becoming a new standard in the industry.
The digital risk score measures the likelihood of a digital asset being compromised or attacked. It is measured by aggregating information from various sources, such as web traffic, DNS records, and other data points.
A plug-and-play solution for your company's digital protection
Digital Risk Protection by Foresiet
Digital risk score is a new way to measure the risk of digital assets, and it is becoming a new standard in the industry.
The digital risk score measures the likelihood of a digital asset being compromised or attacked. It is measured by aggregating information from various sources, such as web traffic, DNS records, and other data points.
A plug-and-play solution for your company's digital protection
-
DTEX InTERCEPT
InTERCEPT is a smart , sophisticated, scalable workforce cyber security solution. With InTERCEPT -- Prevent data loss with behavioural intent intelligence
- Detect insider threats with dynamic risk scoring
- Enrich SOC operations with human telemetry
- Accelerate incident response with real time forensics
DTEX InTERCEPT
InTERCEPT is a smart , sophisticated, scalable workforce cyber security solution. With InTERCEPT -- Prevent data loss with behavioural intent intelligence
- Detect insider threats with dynamic risk scoring
- Enrich SOC operations with human telemetry
- Accelerate incident response with real time forensics
-
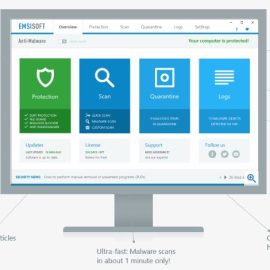
Emsisoft Anti Malware
$9.35 – $265.00 / yearHighlights- Award-winning threat detection
- High performance
- Dual-engine technology
- Advanced smart cleaning
- Cloud Management
- Advance & Persistent Threat Prevention
- Antivirus and Anti-Malware
- EDR Capabilities
- Best Protection against Ransomware
- Anti-Ransomware
- Surf- & Banking-Protection
- Behavior Blocker
- Firewall
- Advance Malware Detection Techniques
- Free Ransomware decryption tools
Emsisoft Anti Malware
Highlights- Award-winning threat detection
- High performance
- Dual-engine technology
- Advanced smart cleaning
- Cloud Management
- Advance & Persistent Threat Prevention
- Antivirus and Anti-Malware
- EDR Capabilities
- Best Protection against Ransomware
- Anti-Ransomware
- Surf- & Banking-Protection
- Behavior Blocker
- Firewall
- Advance Malware Detection Techniques
- Free Ransomware decryption tools
$9.35 – $265.00 / year -
INTELACT
INTELACT offers organizations a fully automated and targeted solution for Attack Surface Monitoring, enabling tailored configuration of client’s assets, automated monitoring of these assets in KELA’s Dark Net sources, and real-time alerting on any compromise or exposure of themINTELACT
INTELACT offers organizations a fully automated and targeted solution for Attack Surface Monitoring, enabling tailored configuration of client’s assets, automated monitoring of these assets in KELA’s Dark Net sources, and real-time alerting on any compromise or exposure of them -
ISMAC Pro
$17.99$15.99 per endpoint/annumWith Case Management and a Threat Intelligence Feed you'll be able to better perform cybersecurity in complex environments with a broad mix of attack surfaces such as cloud, on-premises and personal endpoints.ISMAC Pro
With Case Management and a Threat Intelligence Feed you'll be able to better perform cybersecurity in complex environments with a broad mix of attack surfaces such as cloud, on-premises and personal endpoints.$15.99Was $17.99Save $2 -
ISMAC SOAR
$29.99$25.99 / year with a 14-day free trial and a $6,000.00 sign-up feeFor large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.ISMAC SOAR
Category: Cloud Security Compliance Management Container Security Log Management Malware Detection and Analysis Security Incident Management and Response SOAR Threat Intelligence and Signature Feeds VAPT | SKU: 003For large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.$25.99Was $29.99Save $4 -
MCT EventShield
A MCT EventShield tool is crucial for organizations to monitor and safeguard their assets and data against cyber threats. MCT EventShield functions by collecting security-related data from various sources, such as logs, network traffic, and other security tools.MCT EventShield
A MCT EventShield tool is crucial for organizations to monitor and safeguard their assets and data against cyber threats. MCT EventShield functions by collecting security-related data from various sources, such as logs, network traffic, and other security tools. -
Media Sonar Web Intelligence & Investigation Platform
$28,785.00 / year with a 3-day free trialMedia Sonar is an all-in-one Web Intelligence and Investigation Platform. Our solution broadens the lens of your digital attack surface, securing your brand and assets while strengthen your security operations posture. Equip your security team with visibility into indicators of threat emerging outside of your organization, with intelligence from the Open and Dark Web. Media Sonar works with our clients and partners to deliver personalized 1:1 customer training and support. All questions answered, period.Media Sonar Web Intelligence & Investigation Platform
Media Sonar is an all-in-one Web Intelligence and Investigation Platform. Our solution broadens the lens of your digital attack surface, securing your brand and assets while strengthen your security operations posture. Equip your security team with visibility into indicators of threat emerging outside of your organization, with intelligence from the Open and Dark Web. Media Sonar works with our clients and partners to deliver personalized 1:1 customer training and support. All questions answered, period.$28,785.00 / year with a 3-day free trial -
Mirobase DLP with Employee Monitoring
Lets not just call Mirobase an Employee Monitoring solution, its much more than that. Mirobase can improve productivity, increase revenue, improve profits and safeguard data. Mirobase can be used for- Insider Threat Management
- Employee Monitoring
- User Behavior Analysis - Finding Disloyal Employees, Getting to know in advance who wants to leave job
- Data Leak Prevention
- User management
- Endpoint management
- Most importantly Safeguard Confidential & Crucial Data
Mirobase DLP with Employee Monitoring
Lets not just call Mirobase an Employee Monitoring solution, its much more than that. Mirobase can improve productivity, increase revenue, improve profits and safeguard data. Mirobase can be used for- Insider Threat Management
- Employee Monitoring
- User Behavior Analysis - Finding Disloyal Employees, Getting to know in advance who wants to leave job
- Data Leak Prevention
- User management
- Endpoint management
- Most importantly Safeguard Confidential & Crucial Data
-
Morphisec Breach Prevention Platform
The Morphisec breach prevention platform enables IT and security teams of any size to secure critical systems against the most advanced and disruptive cyberthreats without needing prior knowledge of them. From endpoints to servers to the cloud, Morphisec streamlines cybersecurity and ensures you don’t end up on the news.Morphisec Breach Prevention Platform
The Morphisec breach prevention platform enables IT and security teams of any size to secure critical systems against the most advanced and disruptive cyberthreats without needing prior knowledge of them. From endpoints to servers to the cloud, Morphisec streamlines cybersecurity and ensures you don’t end up on the news. -
oak9 Cloud Infrastructure Security SaaS Platform
$2,000.00oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks.oak9 Cloud Infrastructure Security SaaS Platform
oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks. -
RADARK
KELA’s RADARK delivers automated threat intelligence, cultivating the targeted and contextualized insights – at scale – that you need to stay ahead of attackers. Automatically monitor your environment and ensure that targeted threats are mitigated immediately to consistently maintain a strong security posture.RADARK
KELA’s RADARK delivers automated threat intelligence, cultivating the targeted and contextualized insights – at scale – that you need to stay ahead of attackers. Automatically monitor your environment and ensure that targeted threats are mitigated immediately to consistently maintain a strong security posture.