Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols.IOT Security Penetration Testing
“IOT security should be everyone’s Priority”. Using its unique testing methodology, professionally qualified security services professionals, and high-tech security testing laboratories, Kratikal can help you secure your IoT ecosystem, including IoT applications, cloud APIs, backend servers, and communication protocols. -
Kratikal Vulnerability Assessment & Penetration Testing Service
Kratikal, being a CERT-In Empanelled, provides a Vulnerability Assessment and Penetration Testing (VAPT) security service that focuses on discovering flaws in network, server, and system infrastructure. Organizational security is the emphasis of vulnerability assessment, whereas real-world exploitation is the objective of penetration testing.
Kratikal Vulnerability Assessment & Penetration Testing Service
Kratikal, being a CERT-In Empanelled, provides a Vulnerability Assessment and Penetration Testing (VAPT) security service that focuses on discovering flaws in network, server, and system infrastructure. Organizational security is the emphasis of vulnerability assessment, whereas real-world exploitation is the objective of penetration testing.
-
Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them.Network Penetration Testing
Make your Defenses more resilient against hackers with Network Security. Network testing is a means of examining the present condition of the network's security, including internal, external, and device-level security policies, to find and illustrate weaknesses and assess vulnerabilities. At Kratikal, we use an organized process to identify and prioritize the most vulnerable aspects of your network. The fundamental purpose of a network penetration test is to detect exploitable vulnerabilities in networks, network devices, systems, and hosts so they may be fixed before a hacker discovers and exploits them. -
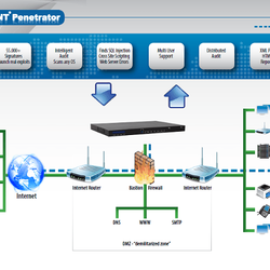
SecPoint Penetrator – VAPT
$250.00 – $12,750.00 / yearSecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.- Discover your weak points before it is too late.
- Ultimate Vulnerability Scanning
- Distributed Scanning Capability. Master / Client mode.
- Hardware 1U Rack or Virtual ESXi,Hyper-V,Linux Images
- Build in Ticket System
- Multiple Reporting: Consultant, Tech, Executive
- Multiple Report Formats: PDF, HTML & XML
- Not fixed on IP adresses, scan unlimited IPs, buy license for simultanous scan
SecPoint Penetrator – VAPT
SecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.- Discover your weak points before it is too late.
- Ultimate Vulnerability Scanning
- Distributed Scanning Capability. Master / Client mode.
- Hardware 1U Rack or Virtual ESXi,Hyper-V,Linux Images
- Build in Ticket System
- Multiple Reporting: Consultant, Tech, Executive
- Multiple Report Formats: PDF, HTML & XML
- Not fixed on IP adresses, scan unlimited IPs, buy license for simultanous scan
$250.00 – $12,750.00 / year -
Securaa – Security Automation Platform
Securaa is a Comprehensive No Code Security Automation Platform that blends intelligence, risk-based asset management, vulnerability insights, automation and incident response into a single platform enabling SOC’s to reduce cybersecurity response time significantly and increase throughput manifolds.- Best RoI in the industry
- Reduce response time by over 95%
- Increase productivity by 300%
- Automate 100% L1 tasks
- Implement in weeks
- Build new playbook in hours
Securaa – Security Automation Platform
Securaa is a Comprehensive No Code Security Automation Platform that blends intelligence, risk-based asset management, vulnerability insights, automation and incident response into a single platform enabling SOC’s to reduce cybersecurity response time significantly and increase throughput manifolds.- Best RoI in the industry
- Reduce response time by over 95%
- Increase productivity by 300%
- Automate 100% L1 tasks
- Implement in weeks
- Build new playbook in hours
-
VAPT by SecurDefense
$29.00A powerful testing practice targeted to analyze how breaches could enable unauthorized access to resources be they the systems, data, network or the applications has to be Penetration Testing Focused to provide security across the extended networks, Penetration tests keep a check on security measures right from the On Premise Enterprise Systems to the Enterprise Mobility solutions and their devices and networks, various websites and web based solutions, right up to the Cloud.VAPT by SecurDefense
A powerful testing practice targeted to analyze how breaches could enable unauthorized access to resources be they the systems, data, network or the applications has to be Penetration Testing Focused to provide security across the extended networks, Penetration tests keep a check on security measures right from the On Premise Enterprise Systems to the Enterprise Mobility solutions and their devices and networks, various websites and web based solutions, right up to the Cloud. -
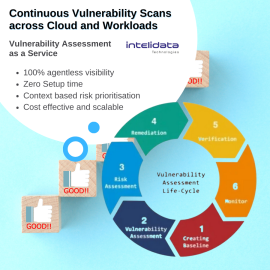
Vulnerability Assessment as a Service by Intelidata
Vulnerability Assessment Tool: Continuous vulnerability scan across clouds and workloads. Context-based prioritization based on exposure and impact. It can cover: Web App Security: Detect, patch security gaps in static websites, complex web apps and APIs Mobile App Security: Automated advanced security assessment of mobile applications - Android, iOS, WindowsVulnerability Assessment as a Service by Intelidata
Vulnerability Assessment Tool: Continuous vulnerability scan across clouds and workloads. Context-based prioritization based on exposure and impact. It can cover: Web App Security: Detect, patch security gaps in static websites, complex web apps and APIs Mobile App Security: Automated advanced security assessment of mobile applications - Android, iOS, Windows -
Vulnerability Assessment by VP Techno Labs
$300.00$250.00Vulnerability Assessment helps businesses to find and fix security flaws quickly in different assets like network infrastructure, Websites, Mobile Applications, Business APIs, Cloud Infrastructure, Home Automation Devices, etc. After Software Development lifecycle, it is recommend to conduct VAPT of that software product, because this will helps businesses to find loopholes in their code, application structure and databases earlier.Vulnerability Assessment by VP Techno Labs
Vulnerability Assessment helps businesses to find and fix security flaws quickly in different assets like network infrastructure, Websites, Mobile Applications, Business APIs, Cloud Infrastructure, Home Automation Devices, etc. After Software Development lifecycle, it is recommend to conduct VAPT of that software product, because this will helps businesses to find loopholes in their code, application structure and databases earlier.