Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
-
Information Security Risk Assessment
$100.00Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysisInformation Security Risk Assessment
Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysis -
Network Penetration Testing
$120.00A technical security assessment that goes beyond the standard port scanning and enumerating vulnerabilities to identify the security risks and their business impact on your network: be it external, internal, or wireless.Network Penetration Testing
A technical security assessment that goes beyond the standard port scanning and enumerating vulnerabilities to identify the security risks and their business impact on your network: be it external, internal, or wireless. -
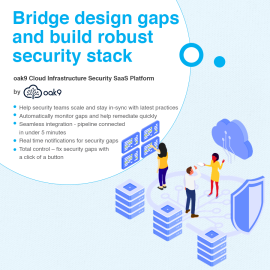
oak9 Cloud Infrastructure Security SaaS Platform
$2,000.00oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks.oak9 Cloud Infrastructure Security SaaS Platform
oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks. -
Red Team Assessments
$100.00Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization.Red Team Assessments
Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization. -
Suite – Enterprise Tier
$1,999.00 / month with a 7-day free trialYou can now automate your red team task. Choose and schedule recurring attack simulations such as Phishing, External/Internal scans, domain scans, Vulnerability Assessments, and more! This includes PDF reports based on your findings with premium support and consultation. Own Your Pentesting: With the Enterprise Suite, CTOs and IT Security Professionals can finally move beyond manual pentesting and get intelligent, automated results. Twice as fast as a pentest and 5x cheaper. You can easily manage, schedule, and review pentests from a single dashboard.Suite – Enterprise Tier
You can now automate your red team task. Choose and schedule recurring attack simulations such as Phishing, External/Internal scans, domain scans, Vulnerability Assessments, and more! This includes PDF reports based on your findings with premium support and consultation. Own Your Pentesting: With the Enterprise Suite, CTOs and IT Security Professionals can finally move beyond manual pentesting and get intelligent, automated results. Twice as fast as a pentest and 5x cheaper. You can easily manage, schedule, and review pentests from a single dashboard.$1 999.00 -
Suite – Premium Tier
$100.00 / monthThis includes 100 Credits delivered monthly to your account! You can schedule what you want, when you need it, at the price you want it. You can now Schedule recurring simulations tests such as Phishing, external scans, domain scans, and more! This includes PDF reports based on your findings with premium support and consultation. Modules cost credits, Modules Included: ● Web Applications: HTTP(S), Source Code, Containerization, ● APIs: SOAP, REST, GraphQL ● Networks: Layers 1-7, Active Directory, LDAP, IPv6, Wireless ● OSINT: Leaked Users, Files ● Amazon Web Services ● Google Cloud Platform ● Microsoft Azure ● Kubernetes: App to Pod, Pod to Worker, Worker to Master, and so on ● Mobile & IoT Applications ● Social Engineering: Phishing, SMSSuite – Premium Tier
This includes 100 Credits delivered monthly to your account! You can schedule what you want, when you need it, at the price you want it. You can now Schedule recurring simulations tests such as Phishing, external scans, domain scans, and more! This includes PDF reports based on your findings with premium support and consultation. Modules cost credits, Modules Included: ● Web Applications: HTTP(S), Source Code, Containerization, ● APIs: SOAP, REST, GraphQL ● Networks: Layers 1-7, Active Directory, LDAP, IPv6, Wireless ● OSINT: Leaked Users, Files ● Amazon Web Services ● Google Cloud Platform ● Microsoft Azure ● Kubernetes: App to Pod, Pod to Worker, Worker to Master, and so on ● Mobile & IoT Applications ● Social Engineering: Phishing, SMS -
User Behaviour Analytics
End users, not the machines, pose the biggest security challenge in the fast-changing IT infrastructure landscape. While compromise of privileged credentials remains one of the most feared IT threats of an enterprise IT security team, more and more IT incidents are stemming from anomalous end user behavioral profiles. Threat Detection and real-time analytics is a need of the hour.
ARCON | User Behaviour Analytics solution offer enterprise IT security teams with necessary tools to crunch a large lake of enterprise data, spot anomalous and risky behavior profiles along with a capability to trigger alerts in real-time.User Behaviour Analytics
End users, not the machines, pose the biggest security challenge in the fast-changing IT infrastructure landscape. While compromise of privileged credentials remains one of the most feared IT threats of an enterprise IT security team, more and more IT incidents are stemming from anomalous end user behavioral profiles. Threat Detection and real-time analytics is a need of the hour.
ARCON | User Behaviour Analytics solution offer enterprise IT security teams with necessary tools to crunch a large lake of enterprise data, spot anomalous and risky behavior profiles along with a capability to trigger alerts in real-time.