Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
Appknox Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) simplified for your mobile apps. See exactly what hackers see. Save your apps from Man in the Middle Attacks (MiTM) with Appknox.Appknox Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) simplified for your mobile apps. See exactly what hackers see. Save your apps from Man in the Middle Attacks (MiTM) with Appknox. -
Appknox Static Application Security Testing
Simplified Static Application Security Testing (SAST) for Mobile App Security- Surface vulnerabilities before they turn into a threat
- Don’t let security become an unpredictable blocker when you go to market
- Integrate security as a regular part of your development cycle without shifting existing practices
Appknox Static Application Security Testing
Simplified Static Application Security Testing (SAST) for Mobile App Security- Surface vulnerabilities before they turn into a threat
- Don’t let security become an unpredictable blocker when you go to market
- Integrate security as a regular part of your development cycle without shifting existing practices
-
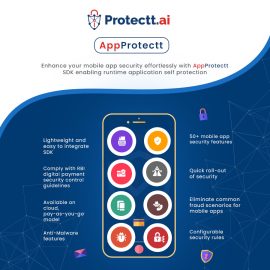
AppProtectt
Light Weight Mobile App Security SDK with 50+ mobile app security capabilities. Plug and Play security for Mobile applications. Protect Mobile App against data leaks, malware exploitations, app tampering, reverse engineering, etc. and ensure customer satisfaction. Lower Total Cost of Ownership Ensure Regulatory Compliances (RBI/SEBI/NPCI) Sector & Geography agnosticAppProtectt
Light Weight Mobile App Security SDK with 50+ mobile app security capabilities. Plug and Play security for Mobile applications. Protect Mobile App against data leaks, malware exploitations, app tampering, reverse engineering, etc. and ensure customer satisfaction. Lower Total Cost of Ownership Ensure Regulatory Compliances (RBI/SEBI/NPCI) Sector & Geography agnostic -
Axiom Protect
$6.00 – $9.60 for 1 yearAxiom Protect 2.0 (AP2) Platform protects your business with automated onboarding, solid identity verification, adaptive and absolute authentication covering secure biometric authentication and data protection while simplifying the multiple applications integration and finally offering an easy login experience for not just employees but also end-users.Axiom Protect
Category: Data Masking Data Security Database Security Fraud Prevention Identity and Access Management Mobile Data Protection |Axiom Protect 2.0 (AP2) Platform protects your business with automated onboarding, solid identity verification, adaptive and absolute authentication covering secure biometric authentication and data protection while simplifying the multiple applications integration and finally offering an easy login experience for not just employees but also end-users.$6.00 – $9.60 for 1 year -
baiMobile Smartcard Reader Framework for Android and iOS
$10.00$9.00baiMobile Smartcard Reader framework is an SDK for mobile device for smartcard based security for secure authentication, secure email communication, digital signing, data encryption and cryptographic operations within a mobile applicationbaiMobile Smartcard Reader Framework for Android and iOS
baiMobile Smartcard Reader framework is an SDK for mobile device for smartcard based security for secure authentication, secure email communication, digital signing, data encryption and cryptographic operations within a mobile application -
Encrypted Phone by Kaymera
NKrypt Phone by Kaymera is a combination of best in class security and premium usability. Off the shelf Google Pixel device powered by Kaymera encrypted OS for your peace of mind and data privacy. The unique solution that protect your smartphone against Pegasus attacks Order a Google Pixel + Kaymera OS from us or purchase a Google Pixel of your choice from a local retailer and buy Kaymera OS separately.Encrypted Phone by Kaymera
NKrypt Phone by Kaymera is a combination of best in class security and premium usability. Off the shelf Google Pixel device powered by Kaymera encrypted OS for your peace of mind and data privacy. The unique solution that protect your smartphone against Pegasus attacks Order a Google Pixel + Kaymera OS from us or purchase a Google Pixel of your choice from a local retailer and buy Kaymera OS separately. -
Indusface Mobile Application Scanner
Indusface Mobile Application Scanning helps businesses secure their apps with in-depth testing. It detects vulnerabilities and insecure permission issues to provide comprehensive reports on readiness of apps to be used on mobile devices safely. With mobile devices and applications becoming the next-big-step for businesses, Indusface Mobile Application Scanning (MAS) helps you take control over their security. It uses a broad combination of mobile application security assessment techniques to find out malware, data leakage, and fraudulent transaction risks.A Dynamic Mobile Application Security Penetration Testing Solution from IndusfaceIndusface Mobile Application Scanner
Indusface Mobile Application Scanning helps businesses secure their apps with in-depth testing. It detects vulnerabilities and insecure permission issues to provide comprehensive reports on readiness of apps to be used on mobile devices safely. With mobile devices and applications becoming the next-big-step for businesses, Indusface Mobile Application Scanning (MAS) helps you take control over their security. It uses a broad combination of mobile application security assessment techniques to find out malware, data leakage, and fraudulent transaction risks.A Dynamic Mobile Application Security Penetration Testing Solution from Indusface -
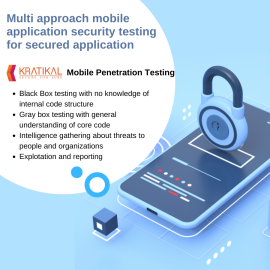
Mobile Application Testing by Kratikal
“The quickest access point to your digital self is now your mobile device.” Mobile application security testing is the process of looking for bugs in the code and other aspects of the application. The overall evaluation process must include a stage called VAPT for mobile applications since it improves in-app security and lowers the chance of fraud, malware infection, data leakage, and other security problems. Organizations are hired to conduct mobile application security testing because cyberattacks are becoming more sophisticated.Mobile Application Testing by Kratikal
“The quickest access point to your digital self is now your mobile device.” Mobile application security testing is the process of looking for bugs in the code and other aspects of the application. The overall evaluation process must include a stage called VAPT for mobile applications since it improves in-app security and lowers the chance of fraud, malware infection, data leakage, and other security problems. Organizations are hired to conduct mobile application security testing because cyberattacks are becoming more sophisticated. -
Secure Communication by KoolSpan Dome
Mobile Secure Communicatoin Solution: exclusive military-grade end-to-end encryption and security for voice calls, messaging and file sharing. Designed to operate on-prem in fully enclosed network environmentsSecure Communication by KoolSpan Dome
Mobile Secure Communicatoin Solution: exclusive military-grade end-to-end encryption and security for voice calls, messaging and file sharing. Designed to operate on-prem in fully enclosed network environments -
T2 COMMUNICATOR
$999.00T2 COMMUNICATOR secures mobile communication and data-at-rest. Engineered for organizations operating in the critical sectors. T2 COMMUNICATOR covers all critical vectors of attack:- hardware
- OS
- applications
- connectivity
T2 COMMUNICATOR
Category: Data-at-Rest Encryption Data-in-Motion Encryption Endpoint Security Messaging Security Mobile Communication Security Mobile Data Protection Mobile Device Management Secure File Transfer Zero trust |T2 COMMUNICATOR secures mobile communication and data-at-rest. Engineered for organizations operating in the critical sectors. T2 COMMUNICATOR covers all critical vectors of attack:- hardware
- OS
- applications
- connectivity
-
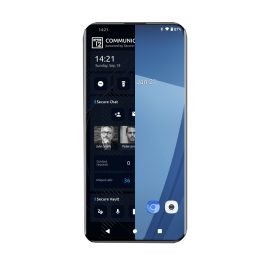
T2 COMMUNICATOR Dual OS
T2 COMMUNICATOR Dual is a unique Dual OS secure device for Professional and Professional use, eliminating the need of carrying multiple phones. It facilitates:
- Two completely separated and hardened operating systems
- Encrypted communication
- Secure file share and storage
- Malware, zero-click spyware, tracking, and IMSI-catcher protection
- Complete management of device permissions and policies
- An optional feature of self-hosting for unmatched security
T2 COMMUNICATOR and T2 COMMUNICATOR Dual
are engineered and trusted by organizations operating in critical sectors.
T2 COMMUNICATOR Dual OS
T2 COMMUNICATOR Dual is a unique Dual OS secure device for Professional and Professional use, eliminating the need of carrying multiple phones. It facilitates:
- Two completely separated and hardened operating systems
- Encrypted communication
- Secure file share and storage
- Malware, zero-click spyware, tracking, and IMSI-catcher protection
- Complete management of device permissions and policies
- An optional feature of self-hosting for unmatched security
T2 COMMUNICATOR and T2 COMMUNICATOR Dual
are engineered and trusted by organizations operating in critical sectors.