Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
1Kosmos BlockID for Customer
$500.00$300.00 / monthProvides Strong Authentication to your customer base to reduce Account Takeover and reduce fraud. 1Kosmos BlockID Customer performs identity verification in 205 countries and can include agent-assisted document verification if required. With the ability to handle over 35 million transactions per day, 1kosmos Block ID Verify delivers 99%+ identity proofing accuracy with 99%+ spoofing and counterfeit detection. In seconds. What’s more, our solutions run 100% on machine learning and computer vision technology with absolute zero human bias or mistakes for both gender and race. As a result, when it comes to guarding against algorithmic bias, our solutions set the global standard. and checks to ensure the ID is valid.1Kosmos BlockID for Customer
Provides Strong Authentication to your customer base to reduce Account Takeover and reduce fraud. 1Kosmos BlockID Customer performs identity verification in 205 countries and can include agent-assisted document verification if required. With the ability to handle over 35 million transactions per day, 1kosmos Block ID Verify delivers 99%+ identity proofing accuracy with 99%+ spoofing and counterfeit detection. In seconds. What’s more, our solutions run 100% on machine learning and computer vision technology with absolute zero human bias or mistakes for both gender and race. As a result, when it comes to guarding against algorithmic bias, our solutions set the global standard. and checks to ensure the ID is valid.$300.00Was $500.00Save $200 -
1Kosmos BlockID for Verify
$4.00$2.75Identity Proofing that includes biometrics, world-wide document scanning and an inter-operable digital wallet. 1Kosmos BlockID Verify performs identity verification in 205 countries and can include agent-assisted document verification if required. SIM Binding, US SSN verification and drivers license verification to AAMVA are optional for additional identity verification. Using machine learning and computer vision technologies along with an intuitive user interface, our solution processes even low quality images in dark lighting. Images are processed through thousands of algorithms catching sophisticated fraudulent documents.1Kosmos BlockID for Verify
Identity Proofing that includes biometrics, world-wide document scanning and an inter-operable digital wallet. 1Kosmos BlockID Verify performs identity verification in 205 countries and can include agent-assisted document verification if required. SIM Binding, US SSN verification and drivers license verification to AAMVA are optional for additional identity verification. Using machine learning and computer vision technologies along with an intuitive user interface, our solution processes even low quality images in dark lighting. Images are processed through thousands of algorithms catching sophisticated fraudulent documents. -
1Kosmos BlockID for Workforce
$200.00$138.00 / monthEliminate Passwords. Avoid Credential Compromises. Provide a more secure and easier way to authenticate. 1Kosmos BlockID Workforce provides workers a new convenient way to login to their VPN and office applications using their likeness or some other biometric in place of a user ID and password. It allows organizations to modernize multi-factor authentication for all logins by eliminating clumsy SMS codes by transparently verifying user identity at every access request. By merging identity verification with authentication, the unique distributed identity platform digitally transforms user onboarding and puts users in control of their own digital identity. This gives IT and security a high-level assurance that they know who is accessing online services and eliminates identity-based attacks preventing account compromise, ransomware and associated network breaches while delivering a superior user experience.1Kosmos BlockID for Workforce
Eliminate Passwords. Avoid Credential Compromises. Provide a more secure and easier way to authenticate. 1Kosmos BlockID Workforce provides workers a new convenient way to login to their VPN and office applications using their likeness or some other biometric in place of a user ID and password. It allows organizations to modernize multi-factor authentication for all logins by eliminating clumsy SMS codes by transparently verifying user identity at every access request. By merging identity verification with authentication, the unique distributed identity platform digitally transforms user onboarding and puts users in control of their own digital identity. This gives IT and security a high-level assurance that they know who is accessing online services and eliminates identity-based attacks preventing account compromise, ransomware and associated network breaches while delivering a superior user experience.$138.00Was $200.00Save $62 -
Accops BioAuth
A fingerprint & facial authentication solution with continuous user environment monitoring that enables organizations to create a trusted environment wherever their users are working from.Accops BioAuth
A fingerprint & facial authentication solution with continuous user environment monitoring that enables organizations to create a trusted environment wherever their users are working from. -
Accops HyID: Converged IAM solution
Adaptive context-aware MFA & SSO for on-premise and cloud applications. It delivers a comprehensive and integrated IAM solution for MFA, SSO, Identity Governance & Administration, and Privileged Access Management.Accops HyID: Converged IAM solution
Adaptive context-aware MFA & SSO for on-premise and cloud applications. It delivers a comprehensive and integrated IAM solution for MFA, SSO, Identity Governance & Administration, and Privileged Access Management. -
Accops HySecure: ZTNA-based Application Access Gateway
ZTNA-based Access Gateway to reduce attack surface even in a perimeter-less hybrid work environment.Accops HySecure: ZTNA-based Application Access Gateway
ZTNA-based Access Gateway to reduce attack surface even in a perimeter-less hybrid work environment. -
Axiom Protect
$6.00 – $9.60 for 1 yearAxiom Protect 2.0 (AP2) Platform protects your business with automated onboarding, solid identity verification, adaptive and absolute authentication covering secure biometric authentication and data protection while simplifying the multiple applications integration and finally offering an easy login experience for not just employees but also end-users.Axiom Protect
Category: Data Masking Data Security Database Security Fraud Prevention Identity and Access Management Mobile Data Protection |Axiom Protect 2.0 (AP2) Platform protects your business with automated onboarding, solid identity verification, adaptive and absolute authentication covering secure biometric authentication and data protection while simplifying the multiple applications integration and finally offering an easy login experience for not just employees but also end-users.$6.00 – $9.60 for 1 year -
BAARIGA
BAARIGA automates Identity, Governance and Administration for your environment. Legacy applications, Main Frames and New Age Applications Included. BAARIGA combines the power of AI and automated workflows to deliver secure and sustainable Identity management solution. BAARIGA helps organizations answer these questions: 1. Who should have access 2. Who has access 3. How is the user accessing the environment 4. How is the user using his accessBAARIGA
BAARIGA automates Identity, Governance and Administration for your environment. Legacy applications, Main Frames and New Age Applications Included. BAARIGA combines the power of AI and automated workflows to deliver secure and sustainable Identity management solution. BAARIGA helps organizations answer these questions: 1. Who should have access 2. Who has access 3. How is the user accessing the environment 4. How is the user using his access -
baiMobile Smartcard Reader Framework for Android and iOS
$10.00$9.00baiMobile Smartcard Reader framework is an SDK for mobile device for smartcard based security for secure authentication, secure email communication, digital signing, data encryption and cryptographic operations within a mobile applicationbaiMobile Smartcard Reader Framework for Android and iOS
baiMobile Smartcard Reader framework is an SDK for mobile device for smartcard based security for secure authentication, secure email communication, digital signing, data encryption and cryptographic operations within a mobile application -
BeyondTrust Active Directory Bridge
BeyondTrust Active Directory Bridge centralizes authentication and configuration management for Unix, Linux, and Mac environments by extending Active Directory’s Kerberos authentication and single sign-on and Group Policy capabilities to these platforms.BeyondTrust Active Directory Bridge
BeyondTrust Active Directory Bridge centralizes authentication and configuration management for Unix, Linux, and Mac environments by extending Active Directory’s Kerberos authentication and single sign-on and Group Policy capabilities to these platforms. -
Block Armour Secure Shield
Block Armour Secure Shield is a Unified Secure Network Access Solution built on Zero Trust powered by SDP and Block Chain that protects Enterprise, Cloud and IOT Network Access scenarios for employees, third-party users and IOT devices and sensors as well. It can be used to ensure a secure WFH/BYOD experience and reduces the attack surface for malware and ransomware.Block Armour Secure Shield
Block Armour Secure Shield is a Unified Secure Network Access Solution built on Zero Trust powered by SDP and Block Chain that protects Enterprise, Cloud and IOT Network Access scenarios for employees, third-party users and IOT devices and sensors as well. It can be used to ensure a secure WFH/BYOD experience and reduces the attack surface for malware and ransomware. -
Calico Cloud
$36.50Calico Cloud is the industry’s only active Cloud-Native Application Protection Platform (CNAPP) with full-stack observability. It enables organizations to prevent attacks using zero trust, and to detect, troubleshoot, and automatically mitigate vulnerabilities and security threats in build, deploy, and runtime stages across multi-cloud and hybrid deployments. Calico Cloud supports multiple dataplanes including eBPF, Windows and Linux. With Calico Cloud, users get a fully managed pay-as-you-go SaaS platform for active build and runtime security of cloud-native applications running on containers and Kubernetes.Calico Cloud
Calico Cloud is the industry’s only active Cloud-Native Application Protection Platform (CNAPP) with full-stack observability. It enables organizations to prevent attacks using zero trust, and to detect, troubleshoot, and automatically mitigate vulnerabilities and security threats in build, deploy, and runtime stages across multi-cloud and hybrid deployments. Calico Cloud supports multiple dataplanes including eBPF, Windows and Linux. With Calico Cloud, users get a fully managed pay-as-you-go SaaS platform for active build and runtime security of cloud-native applications running on containers and Kubernetes. -
Identity as Powered Services by Inspirit Vision
Identity-as-a-Powered Service (IDaaS) is a hosted cloud-based identity and access management (IAM) solution that is run by a reliable third party. IDaaS combines the operational and financial advantages of a cloud-based service delivery model with all the features and advantages of an enterprise-class identity access management solution.Identity as Powered Services by Inspirit Vision
Identity-as-a-Powered Service (IDaaS) is a hosted cloud-based identity and access management (IAM) solution that is run by a reliable third party. IDaaS combines the operational and financial advantages of a cloud-based service delivery model with all the features and advantages of an enterprise-class identity access management solution. -
Identity Manager by One Idenity
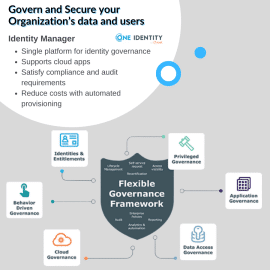
Identity Manager governs and secures your organization’s data and users, meets uptime requirements, reduces risk and satisfies compliance by giving users access to data and applications they need - and only what they need - whether on-premises, hybrid or in the cloud. Now, identity security can be driven by business needs, not by IT capabilities. With Identity Manager, you can unify security policies and satisfy governance needs — today and long into the future.Identity Manager by One Idenity
Identity Manager governs and secures your organization’s data and users, meets uptime requirements, reduces risk and satisfies compliance by giving users access to data and applications they need - and only what they need - whether on-premises, hybrid or in the cloud. Now, identity security can be driven by business needs, not by IT capabilities. With Identity Manager, you can unify security policies and satisfy governance needs — today and long into the future. -
Identity Verification by SurePass
We provide the best available Identity Verification API in the market. Our online identity verification APIs are not only error free but also super-fast.
- Easy to integrate REST APIs with 24×7 Tech Support
- AI based Advanced OCR for all Govt. issued IDs
- Match customer’s selfie with the face on ID card
- Instant verification with Real-time APIs
Identity Verification by SurePass
We provide the best available Identity Verification API in the market. Our online identity verification APIs are not only error free but also super-fast.
- Easy to integrate REST APIs with 24×7 Tech Support
- AI based Advanced OCR for all Govt. issued IDs
- Match customer’s selfie with the face on ID card
- Instant verification with Real-time APIs
-
Information Security Risk Assessment
$100.00Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysisInformation Security Risk Assessment
Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysis