Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
-
Governance, Risk and Compliance by Cyber Sierra
Take Complexity and Guesswork Out of Compliance
Comply with regulations, unlock sales and continuously monitor regulatory processes with recognised certifications (ISO27001, SOC2, HIPAA, PCIDSS, GDPR, etc.).
Manage Risks Seamlessly Across Your Organization
Map your assets automatically. Understand your assets’ context and relationships with users. Provide a seamless platform to assess and manage risks for everyone.
Governance, Risk and Compliance by Cyber Sierra
Take Complexity and Guesswork Out of Compliance
Comply with regulations, unlock sales and continuously monitor regulatory processes with recognised certifications (ISO27001, SOC2, HIPAA, PCIDSS, GDPR, etc.).
Manage Risks Seamlessly Across Your Organization
Map your assets automatically. Understand your assets’ context and relationships with users. Provide a seamless platform to assess and manage risks for everyone.
-
Information Archive
Information Archiving helps organisations meet GDPR and other regulatory requirements by securing and managing critical data. The solution stores an unlimited number of files and communications across email, SMS, and emerging platforms like Microsoft Teams and social media. It helps protect your organisation against compliance violations and unplanned litigations and is an essential replacement for organisations moving off of aging, on-premises, email-only hardware.Information Archive
Category: Cloud Security Compliance Management Cyber Security Services Data Breach Protection Data Discovery Data Security |Information Archiving helps organisations meet GDPR and other regulatory requirements by securing and managing critical data. The solution stores an unlimited number of files and communications across email, SMS, and emerging platforms like Microsoft Teams and social media. It helps protect your organisation against compliance violations and unplanned litigations and is an essential replacement for organisations moving off of aging, on-premises, email-only hardware. -
Information Security Risk Assessment
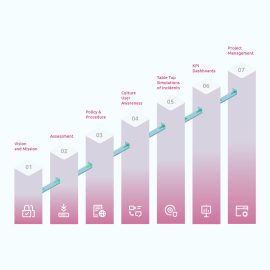
$100.00Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysisInformation Security Risk Assessment
Performing a comprehensive Risk Assessment on the identified critical IT assets would enable the selection of appropriate risk mitigation controls. Intect’s Risk assessment methodology is a multi-fold activity comprising assigning values to the identified critical information assets, threat assessment, & gap analysis -
Invinsense Compliance
Invinsense GSOS solutions and services help your organizations achieve the necessary compliance needed because of your industry and geography. Our intuitive solution and expert Pink team help you implement frameworks like ISO, NIST, SOC-2, etc without the frustration of complexity and confusion of documentation. We help you achieve smooth processes, documentation and needed awareness to achieve not only compliance, but also preparedness of any scale of cyberattack. We help you achieve peace of mind to continue doing your core business.Invinsense Compliance
Invinsense GSOS solutions and services help your organizations achieve the necessary compliance needed because of your industry and geography. Our intuitive solution and expert Pink team help you implement frameworks like ISO, NIST, SOC-2, etc without the frustration of complexity and confusion of documentation. We help you achieve smooth processes, documentation and needed awareness to achieve not only compliance, but also preparedness of any scale of cyberattack. We help you achieve peace of mind to continue doing your core business. -
ISMAC SOAR
$29.99$25.99 / year with a 14-day free trial and a $6,000.00 sign-up feeFor large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.ISMAC SOAR
Category: Cloud Security Compliance Management Container Security Log Management Malware Detection and Analysis Security Incident Management and Response SOAR Threat Intelligence and Signature Feeds VAPT | SKU: 003For large and complex environments ISMAC SOAR will enable your team to achieve scalability of your cyberdefense efforts.$25.99Was $29.99Save $4 -
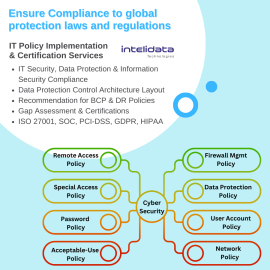
IT Policy and Certification Services by Intelidata
Review & Implementation of IS/IT Policies and IS/IT controls for their adequacy and effectiveness vis-à-vis frameworks/standards of ISO 27001:2022, IT Act 2008 & Cert-in guidelines.- IT Security, Data Protection & Information Security Compliance's Control Implementation
- Data Protection Control Architecture Layout as per new emerging Cyber Risks & Threats
- Recommendation for BCP & DR policies
- ISMS and Information Security Awareness Trainings for IT Staff
IT Policy and Certification Services by Intelidata
Review & Implementation of IS/IT Policies and IS/IT controls for their adequacy and effectiveness vis-à-vis frameworks/standards of ISO 27001:2022, IT Act 2008 & Cert-in guidelines.- IT Security, Data Protection & Information Security Compliance's Control Implementation
- Data Protection Control Architecture Layout as per new emerging Cyber Risks & Threats
- Recommendation for BCP & DR policies
- ISMS and Information Security Awareness Trainings for IT Staff
-
Network Penetration Testing
$120.00A technical security assessment that goes beyond the standard port scanning and enumerating vulnerabilities to identify the security risks and their business impact on your network: be it external, internal, or wireless.Network Penetration Testing
A technical security assessment that goes beyond the standard port scanning and enumerating vulnerabilities to identify the security risks and their business impact on your network: be it external, internal, or wireless. -
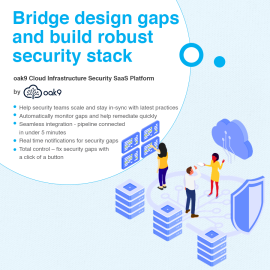
oak9 Cloud Infrastructure Security SaaS Platform
$2,000.00oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks.oak9 Cloud Infrastructure Security SaaS Platform
oak9 lets you tailor security standards to your needs and intelligently learns the more you build, so you aren’t slowed by hundreds of false positives or non-relevant exceptions. You can focus on the functional capabilities of your application while oak9 assess every change to your application architecture against your customized security blueprint to notify you in real-time of any risks. -
Red Team Assessments
$100.00Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization.Red Team Assessments
Red Team engagements can demonstrate the risk posed by an APT (Advanced Persistent Threat). These types of comprehensive, complex security assessments are best used by companies looking to improve the security maturity of the organization. -
Regulatory Compliance
The observance of rules, regulations, and norms that are pertinent to an organization's business processes is referred to as regulatory compliance. Processes and strategies for regulatory compliance, offer firms direction as they work to achieve their commercial objectives. Consumers trust businesses that strictly adhere to legal requirements aimed to secure personal data while data breaches tend to continue to occur more frequently in an unprotected environmentRegulatory Compliance
The observance of rules, regulations, and norms that are pertinent to an organization's business processes is referred to as regulatory compliance. Processes and strategies for regulatory compliance, offer firms direction as they work to achieve their commercial objectives. Consumers trust businesses that strictly adhere to legal requirements aimed to secure personal data while data breaches tend to continue to occur more frequently in an unprotected environment -
Security Compliance Management
ARCON | Security Compliance Management (SCM) is a highly effective enterprise-grade solution to identify, assess and mitigate system vulnerabilities. ARCON|SCM automates the entire risk assessment process, manages execution and generates detailed review documentation of IT risk factors. The vulnerability assessment solution enhances IT controls and visibility by setting-up baseline security configurations and policies for disparate technology platforms. Enterprise IT risk management teams find ARCON| SCM as a robust technology to adhere to various IT security standards for compliance purposes as well.Security Compliance Management
ARCON | Security Compliance Management (SCM) is a highly effective enterprise-grade solution to identify, assess and mitigate system vulnerabilities. ARCON|SCM automates the entire risk assessment process, manages execution and generates detailed review documentation of IT risk factors. The vulnerability assessment solution enhances IT controls and visibility by setting-up baseline security configurations and policies for disparate technology platforms. Enterprise IT risk management teams find ARCON| SCM as a robust technology to adhere to various IT security standards for compliance purposes as well. -
Software Compliance Audit & Management by SecurDefense
$3,000.00Our passion is to give our customers the absolutely correct view of all their software Products Deployments. Microsoft, Autodesk, Adobe, Oracle products from 136 global software publishers are tracked by our application. . We will install Euladox Auditor on premise & train you on conducting discovery across the network. Conduct Discovery across your network domains & on systems not connected to the network. We will analyze data, run the software recognition engine and map the discovered programs to deployed licenses. We provide a deployment & compliance report for all products installed across your enterprise.Software Compliance Audit & Management by SecurDefense
Our passion is to give our customers the absolutely correct view of all their software Products Deployments. Microsoft, Autodesk, Adobe, Oracle products from 136 global software publishers are tracked by our application. . We will install Euladox Auditor on premise & train you on conducting discovery across the network. Conduct Discovery across your network domains & on systems not connected to the network. We will analyze data, run the software recognition engine and map the discovered programs to deployed licenses. We provide a deployment & compliance report for all products installed across your enterprise. -
Standard Compliance
An organization's set of rules and regulations that are specialized to a given industry. In other terms, statutory compliance is the act of scrupulously upholding norms that businesses are compelled to adhere to. In order to protect customer data, the company must follow industry standards. Kratikal helps organizations get compliances for ISO27001, GDPR,HIPAA, SOC 1, SOC 2, and PCI DSSStandard Compliance
An organization's set of rules and regulations that are specialized to a given industry. In other terms, statutory compliance is the act of scrupulously upholding norms that businesses are compelled to adhere to. In order to protect customer data, the company must follow industry standards. Kratikal helps organizations get compliances for ISO27001, GDPR,HIPAA, SOC 1, SOC 2, and PCI DSS -
Suite – Enterprise Tier
$1,999.00 / month with a 7-day free trialYou can now automate your red team task. Choose and schedule recurring attack simulations such as Phishing, External/Internal scans, domain scans, Vulnerability Assessments, and more! This includes PDF reports based on your findings with premium support and consultation. Own Your Pentesting: With the Enterprise Suite, CTOs and IT Security Professionals can finally move beyond manual pentesting and get intelligent, automated results. Twice as fast as a pentest and 5x cheaper. You can easily manage, schedule, and review pentests from a single dashboard.Suite – Enterprise Tier
You can now automate your red team task. Choose and schedule recurring attack simulations such as Phishing, External/Internal scans, domain scans, Vulnerability Assessments, and more! This includes PDF reports based on your findings with premium support and consultation. Own Your Pentesting: With the Enterprise Suite, CTOs and IT Security Professionals can finally move beyond manual pentesting and get intelligent, automated results. Twice as fast as a pentest and 5x cheaper. You can easily manage, schedule, and review pentests from a single dashboard.$1 999.00 -
Suite – Premium Tier
$100.00 / monthThis includes 100 Credits delivered monthly to your account! You can schedule what you want, when you need it, at the price you want it. You can now Schedule recurring simulations tests such as Phishing, external scans, domain scans, and more! This includes PDF reports based on your findings with premium support and consultation. Modules cost credits, Modules Included: ● Web Applications: HTTP(S), Source Code, Containerization, ● APIs: SOAP, REST, GraphQL ● Networks: Layers 1-7, Active Directory, LDAP, IPv6, Wireless ● OSINT: Leaked Users, Files ● Amazon Web Services ● Google Cloud Platform ● Microsoft Azure ● Kubernetes: App to Pod, Pod to Worker, Worker to Master, and so on ● Mobile & IoT Applications ● Social Engineering: Phishing, SMSSuite – Premium Tier
This includes 100 Credits delivered monthly to your account! You can schedule what you want, when you need it, at the price you want it. You can now Schedule recurring simulations tests such as Phishing, external scans, domain scans, and more! This includes PDF reports based on your findings with premium support and consultation. Modules cost credits, Modules Included: ● Web Applications: HTTP(S), Source Code, Containerization, ● APIs: SOAP, REST, GraphQL ● Networks: Layers 1-7, Active Directory, LDAP, IPv6, Wireless ● OSINT: Leaked Users, Files ● Amazon Web Services ● Google Cloud Platform ● Microsoft Azure ● Kubernetes: App to Pod, Pod to Worker, Worker to Master, and so on ● Mobile & IoT Applications ● Social Engineering: Phishing, SMS