Description
Review & Implementation of IS/IT Policies and IS/IT controls for their adequacy and effectiveness vis-à-vis frameworks/standards of ISO 27001:2022, IT Act 2008 & Cert-in guidelines covers:
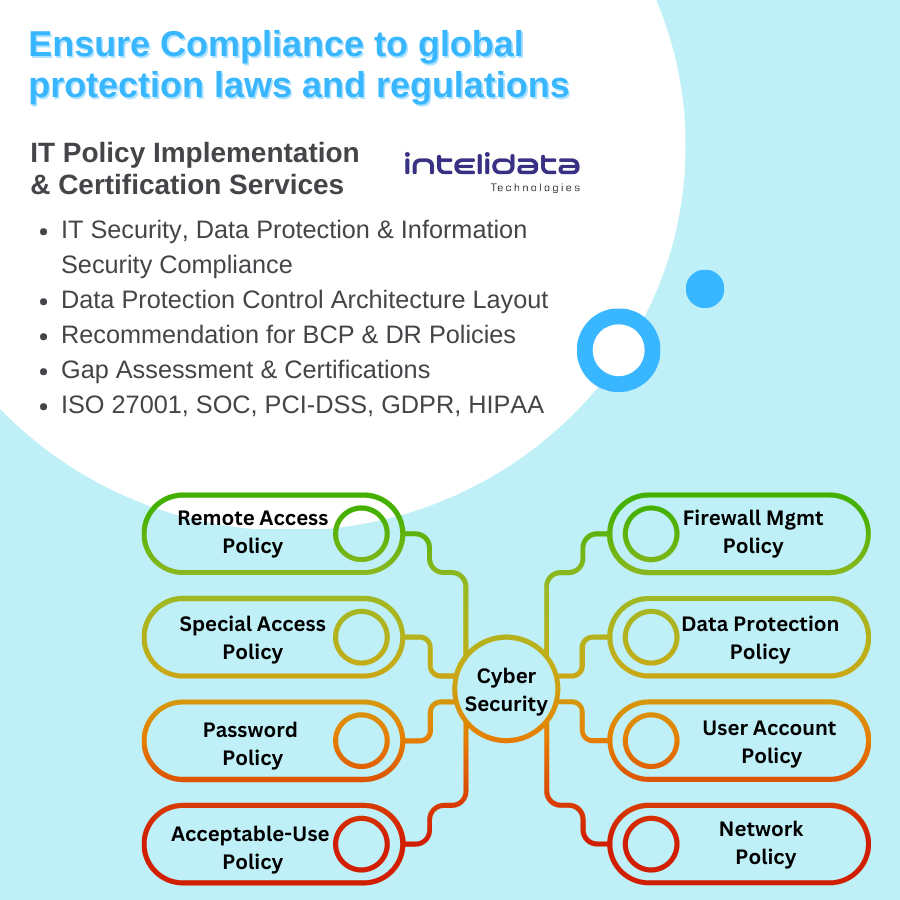
- IT Security, Data Protection & Information Security Compliance’s Control Implementation
- Data Protection Control Architecture Layout as per new emerging Cyber Risks & Threats
- Recommendation for BCP & DR policies – BCP/DR should be tested and updated to ensure its effectiveness in the event of a disaster and its continuing relevance to your Business.
- ISMS and Information Security Awareness Trainings for IT Staff
- Security Awareness Mechanism periodic exercises & Drills for Staff & Management
- Annual Technical Support & Active Assistance Onsite & Off-site for Cyber Security Control
- Suggest security policy documentation as per Cert-in
It is done through following phases:
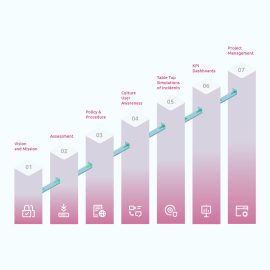
Phase I – Gap Assessment Process
Determine which sections of ISO, are applicable to your business operations. We interview key management and IT personnel to identify the controls which need to be in place to meet the compliance requirement. Once walkthroughs have been completed, we prepare a detailed report on gap analysis which includes specific remediation steps the client must perform to pass each control. This phase will cover following 3 processes:
a) Asset Identification: collect complete list of assets mapped with asset owners and risk owners, which include all documents like policy documents, process documents, list of all devices etc. with their versions etc.
b) Asset Prioritization / Characterization: determine value, productivity, and the importance of the assets in terms of the criticality and categorize assets into three categories in terms of (a) People, (b) Policy/Process, and (c) Technology.
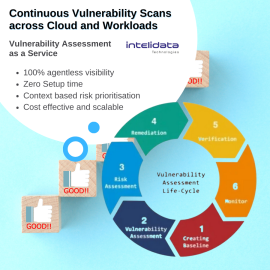
c) Technology (Configuration Assessment / Vulnerability Assessment and System Security Audit): identify Threat and Vulnerability associated with People, Process and Technology
Policy (ISMS Policy, Document Control Policy, Access Control Policy, Malware Protection Policy, Password Security Policy, Log Management Policy, Encryption Policy, Backup Policy, Incident Response Policy, Change Management Policy, Data Security Policy, Network Management Policy, Vulnerability Management Policy, Risk Management Policy, Asset Management Policy, Internet and Email Access Policy, Password Security Policy, Others)
Process (Incident Response, Business Continuity, Disaster Recovery, Data Security (at rest, at motion), Change Management Policy, Fraud Management, Access Control, Vulnerability Management, Backup, Malware Protection, Others
Technology (Endpoints: Windows desktops / laptops / tablets, Servers: Active Directory, Database Server, Application Server, others, Network Devices: Switches, Routers, Wireless Controllers, Others, Security Devices: Firewall, IDS/IPS, DLP (If any))
Phase II – Recommendations:
Remediation recommendations to close the vulnerabilities identified. Detailed steps (wherever / whenever applicable) to be followed while mitigating the reported vulnerabilities. Security issues that pose an imminent threat to the system are to be reported immediately. Submission of Gap Closure Plan and its acceptance by Client
Phase III – Implementation and Retest:
After the submission of interim report & recommendations, fix the identified vulnerability. Thereafter, perform a retest to validate the newly implemented controls mitigate the original risk. The scope of a retest should consider whether any changes occurring as a result of remediation identified from the test are classified as significant.
Phase IV – Final Report & Certification by a Certifying Body:
After the retest is performed, submit its final report and readiness for ISO 27001:2022, Cert-in Certification.
Intelidata also provides similar services for ISO 9001, SOC, PCI-DSS, GDPR, HIPAA , UIDAI – AUA KUA, SOX Compliance, Cyber Security Maturity Model Certification (CMMC) and more.










Description
Technical Experience
We are a qualified & highly technical team of Experienced Cyber Security Researchers, with cumulative experience of 25+ years. We partner with small to mid-sized companies to secure their businesses with easy step-by-step proven processes & Cert-in guidelines.
24/7 Services
We offer round-the-clock technical assistance. We never turn the cell phone off. It’s on 24/7 and it gets answered whenever you call, to give you timely deliveries. By outsourcing your IT security to us, you can focus on what you do best–running your business.
Flexible Pricing
No unexpected bills. No budget blow-outs. No missed deadlines. No broken promises. No shoddy service. No surprises. We believe in adding value to your business and provide meaningful service at a very cost efficient and budget -friendly pricing.
Training Assistance
We provide detailed steps & Cyber Security training to your Web Administrators and Developers for patching. No matter the budget, we pride ourselves on providing comprehensive professional assistance to them to secure your business.