Product categories
- Application Security
- Automotive Cyber Security
- Cloud Access Security Broker
- Cloud Security
- Cyber Security Services
- Data Security
- Endpoint Security
- Forensics
- Governance Risk Management & Compliance
- Infrastructure Security
- Mobile Security
- Network Security
- Password Manager
- Patch Configuration and Management
- Secure File Transfer
- Secure Web Gateway
- Security Information and Event Management
- Security Training Software
- Unified Threat Management
- User Security
- VAPT
-
Cloud Security Assessments
$150.00A technical security assessment for cloud-deployed applications to assess for bad exposures, vulnerabilities, and deviations from the best practices. Cloud security assessments checks for vulnerabilities emerging from unintended network accessibility, misconfigurations, user accounts, and their permissions, access management, and so on.Cloud Security Assessments
A technical security assessment for cloud-deployed applications to assess for bad exposures, vulnerabilities, and deviations from the best practices. Cloud security assessments checks for vulnerabilities emerging from unintended network accessibility, misconfigurations, user accounts, and their permissions, access management, and so on. -
Cloud Security Services by Intelidata
CDL Cloud Security Services help clients secure their cloud migration and transformation journey to build a cyber- resilient and IT compliant cloud ecosystem. Our offerings include:- Cloud security strategy and architecture
- Cloud security assessment services
- Cloud managed security services
- Cloud security governance
- Cloud security solutions in implementation and support
Cloud Security Services by Intelidata
CDL Cloud Security Services help clients secure their cloud migration and transformation journey to build a cyber- resilient and IT compliant cloud ecosystem. Our offerings include:- Cloud security strategy and architecture
- Cloud security assessment services
- Cloud managed security services
- Cloud security governance
- Cloud security solutions in implementation and support
-
Compromise Assessment by SecurDefense
$4,500.00Compromise Assessment involves proactively searching for malware and attackers on your network which maybe present for sometime. They can silently exfiltrate data, listen patiently to confidential data or scan the network to get credentials strong enough to steal key information.Compromise Assessment by SecurDefense
Compromise Assessment involves proactively searching for malware and attackers on your network which maybe present for sometime. They can silently exfiltrate data, listen patiently to confidential data or scan the network to get credentials strong enough to steal key information. -
Cyber Security Consulting Services by Athena Dynamics
Athena Dynamics is a pure-play cyber security consulting arm of BH Global which is fully independent of any state-level relationship. This gives Athena Dynamics the full neutrality and trust of regional and global customers to assist with cyber protection of their Enterprise Information Technology platforms (IT), Industrial Control Operation Technology Systems (OT) and not least, Critical National Info-Infrastructures (CNII). The Good Hackers’ Alliance (“gha”) formed by Athena Dynamics delivers best practices via custom mix of credible and ethical hacker groups with state-level competencies. gha has since fulfilled more than 40 vulnerability assessments for sensitive establishments, as well as recovery operations necessitated by cyber related breaches.Cyber Security Consulting Services by Athena Dynamics
Athena Dynamics is a pure-play cyber security consulting arm of BH Global which is fully independent of any state-level relationship. This gives Athena Dynamics the full neutrality and trust of regional and global customers to assist with cyber protection of their Enterprise Information Technology platforms (IT), Industrial Control Operation Technology Systems (OT) and not least, Critical National Info-Infrastructures (CNII). The Good Hackers’ Alliance (“gha”) formed by Athena Dynamics delivers best practices via custom mix of credible and ethical hacker groups with state-level competencies. gha has since fulfilled more than 40 vulnerability assessments for sensitive establishments, as well as recovery operations necessitated by cyber related breaches. -
Cyber Security Training by Cyber Sierra
Your Greatest Asset can be Your Weakest Link
Employees are your greatest asset. But they may also be your weakest link. Ensure your employees are trained to be cyber-aware and cyber-ready.
- Ensure your employees are aware of cyber security risks
- Run employee awareness training regularly
- Help your employees detect phishing emails and landing pages
- Run counter-phishing campaigns regularly
Cyber Security Training by Cyber Sierra
Your Greatest Asset can be Your Weakest Link
Employees are your greatest asset. But they may also be your weakest link. Ensure your employees are trained to be cyber-aware and cyber-ready.
- Ensure your employees are aware of cyber security risks
- Run employee awareness training regularly
- Help your employees detect phishing emails and landing pages
- Run counter-phishing campaigns regularly
-
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
CyberQ ORO
CyberQ ORO helps security leaders in enterprises measure, communicate and reduce human risk to keep their companies safe from cyber threats. One of the most challenging aspects of building a cybersecurity program is the human risk component.
CyberQ ORO provides a way to quantify this human risk across the entire organization using security incident data, automated assessments & training. Quantifying human risk and analyzing it as part of an overall cyber risk framework provides unique insights to security teams & leaders.
-
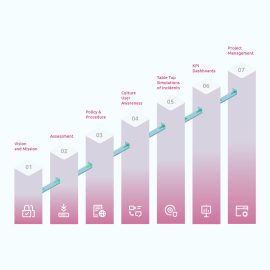
Cyberstanc Ransomware Assessment and Simulation Testing
PHASES OF RANSOMWARE ASSESSMENT and SIMULATION TEST- Ransomware Impact Assessment and isolation
- Ransomware evidence and reverse engineering
- Ransomware recovery process
- Ransomware Sanitization process
- Documentation and report briefing
- Ransomware Prevention and Lessons Learned
- Detect early-stage ransomware attacks and families name
- Identify specific assets that ransomware exploits
- Recognize operational deficiencies by simulating various known and unknown ransomware
- Conduct root cause analysis of ransomware
Cyberstanc Ransomware Assessment and Simulation Testing
PHASES OF RANSOMWARE ASSESSMENT and SIMULATION TEST- Ransomware Impact Assessment and isolation
- Ransomware evidence and reverse engineering
- Ransomware recovery process
- Ransomware Sanitization process
- Documentation and report briefing
- Ransomware Prevention and Lessons Learned
- Detect early-stage ransomware attacks and families name
- Identify specific assets that ransomware exploits
- Recognize operational deficiencies by simulating various known and unknown ransomware
- Conduct root cause analysis of ransomware
-
Data Breach Assessment Testing by VP Techno Labs
$800.00$650.00Data Breach Assessment Testing is specially for organizations who want to avoid and prevent heavy fines and compliance violation and Legal disputes regarding Customer's Data. We uses combination of Forensics, Infrastructure Testing and DRE Approach to make this happen. This will covers more scope than traditional RED/Blue Teaming. Moreover we uses proprietary approach Triple Shield DRE(USP) To secure your infrastructure from every perspective. This testing also prepares an organization to be compliant with different National/International Compliance & Regulations Like SOC, HIPAA, GDPR, CCPA, ISO, NIST, FISMA. So that's the main advantage!Data Breach Assessment Testing by VP Techno Labs
Data Breach Assessment Testing is specially for organizations who want to avoid and prevent heavy fines and compliance violation and Legal disputes regarding Customer's Data. We uses combination of Forensics, Infrastructure Testing and DRE Approach to make this happen. This will covers more scope than traditional RED/Blue Teaming. Moreover we uses proprietary approach Triple Shield DRE(USP) To secure your infrastructure from every perspective. This testing also prepares an organization to be compliant with different National/International Compliance & Regulations Like SOC, HIPAA, GDPR, CCPA, ISO, NIST, FISMA. So that's the main advantage!$650.00Was $800.00Save $150 -
DevSecOps Consulting Services by Intelidata
Intelidata Technologies has a suite of DevSecOps-ready Consultancy services to enable secure continuous delivery, integrated security testing and cloud native delivery pipelines as per Cert-in guidelines. If you haven’t already begun the process, the time is now to merge your security goals with DevOps and implement ‘Security as Code’ DevSecOps best practices.DevSecOps Consulting Services by Intelidata
Intelidata Technologies has a suite of DevSecOps-ready Consultancy services to enable secure continuous delivery, integrated security testing and cloud native delivery pipelines as per Cert-in guidelines. If you haven’t already begun the process, the time is now to merge your security goals with DevOps and implement ‘Security as Code’ DevSecOps best practices. -
DTEX InTERCEPT
InTERCEPT is a smart , sophisticated, scalable workforce cyber security solution. With InTERCEPT -- Prevent data loss with behavioural intent intelligence
- Detect insider threats with dynamic risk scoring
- Enrich SOC operations with human telemetry
- Accelerate incident response with real time forensics
DTEX InTERCEPT
InTERCEPT is a smart , sophisticated, scalable workforce cyber security solution. With InTERCEPT -- Prevent data loss with behavioural intent intelligence
- Detect insider threats with dynamic risk scoring
- Enrich SOC operations with human telemetry
- Accelerate incident response with real time forensics
-
HIPAA Compliance Audit by SecurDefense
$7,000.00The impact of Electronic Standardization, there was an increased risk to security confidentiality and privacy of individually identifiable health information. HIPAA and the importance of the web has clearly steered healthcare’s E-commerce Re-engineering with special emphasis on the administrative simplification provisions that includes benefits, costs and penalties. These provisions incorporate electronic signature, national identifiers, transactions and code sets, privacy, and security. SecurDefense HIPAA Compliance audits organizations security measures and ensures organization is HIPAA compliant.HIPAA Compliance Audit by SecurDefense
The impact of Electronic Standardization, there was an increased risk to security confidentiality and privacy of individually identifiable health information. HIPAA and the importance of the web has clearly steered healthcare’s E-commerce Re-engineering with special emphasis on the administrative simplification provisions that includes benefits, costs and penalties. These provisions incorporate electronic signature, national identifiers, transactions and code sets, privacy, and security. SecurDefense HIPAA Compliance audits organizations security measures and ensures organization is HIPAA compliant. -
Identity as Powered Services by Inspirit Vision
Identity-as-a-Powered Service (IDaaS) is a hosted cloud-based identity and access management (IAM) solution that is run by a reliable third party. IDaaS combines the operational and financial advantages of a cloud-based service delivery model with all the features and advantages of an enterprise-class identity access management solution.Identity as Powered Services by Inspirit Vision
Identity-as-a-Powered Service (IDaaS) is a hosted cloud-based identity and access management (IAM) solution that is run by a reliable third party. IDaaS combines the operational and financial advantages of a cloud-based service delivery model with all the features and advantages of an enterprise-class identity access management solution. -
Information Archive
Information Archiving helps organisations meet GDPR and other regulatory requirements by securing and managing critical data. The solution stores an unlimited number of files and communications across email, SMS, and emerging platforms like Microsoft Teams and social media. It helps protect your organisation against compliance violations and unplanned litigations and is an essential replacement for organisations moving off of aging, on-premises, email-only hardware.Information Archive
Category: Cloud Security Compliance Management Cyber Security Services Data Breach Protection Data Discovery Data Security |Information Archiving helps organisations meet GDPR and other regulatory requirements by securing and managing critical data. The solution stores an unlimited number of files and communications across email, SMS, and emerging platforms like Microsoft Teams and social media. It helps protect your organisation against compliance violations and unplanned litigations and is an essential replacement for organisations moving off of aging, on-premises, email-only hardware. -
Invinsense Compliance
Invinsense GSOS solutions and services help your organizations achieve the necessary compliance needed because of your industry and geography. Our intuitive solution and expert Pink team help you implement frameworks like ISO, NIST, SOC-2, etc without the frustration of complexity and confusion of documentation. We help you achieve smooth processes, documentation and needed awareness to achieve not only compliance, but also preparedness of any scale of cyberattack. We help you achieve peace of mind to continue doing your core business.Invinsense Compliance
Invinsense GSOS solutions and services help your organizations achieve the necessary compliance needed because of your industry and geography. Our intuitive solution and expert Pink team help you implement frameworks like ISO, NIST, SOC-2, etc without the frustration of complexity and confusion of documentation. We help you achieve smooth processes, documentation and needed awareness to achieve not only compliance, but also preparedness of any scale of cyberattack. We help you achieve peace of mind to continue doing your core business. -
Invinsense MDR
INVINSENSE MDR DO DETECTION, THREAT HUNTING, AND RESPONSE FOR CISOS The main objective of Invinsense MDR is to identify potentially malicious activities across your technology landscape and neutralize them on behalf of CISOs or incoordination of CISOInvinsense MDR
INVINSENSE MDR DO DETECTION, THREAT HUNTING, AND RESPONSE FOR CISOS The main objective of Invinsense MDR is to identify potentially malicious activities across your technology landscape and neutralize them on behalf of CISOs or incoordination of CISO -
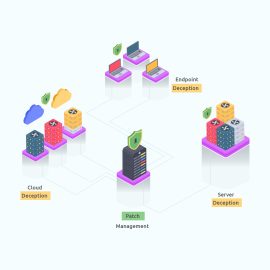
Invinsense MDR+
Invinsense Managed Detection and Response Plus Invinsense MDR+ - MDR Services That Leverage Deception, Patch Management and Network Intrusion Detection System (NIDS)Invinsense MDR+
Invinsense Managed Detection and Response Plus Invinsense MDR+ - MDR Services That Leverage Deception, Patch Management and Network Intrusion Detection System (NIDS)