Description
SecPoint Penetrator can help you to find the vulnerabilities on your entire network. You can scan your internal local IP addresses and your public IPs available on the Internet. You can scan your Websites, webapps, servers, workstations, IoT, scada etc. Find all SSL vulnarabilities. SecPoint State of the art Cyber Security and must have for every organization. SecPoint can be installed as harware appliance or virtual machine.
You may find vulnerabilities automatically with the schedule scanning & get notified by email once new vulnerabilities are discovered. PDF & HTML reports will show you the evidence of vulnerabilities and information on how to eliminate them.
SecPoint is fully featured powerful yet easy to use Vulnerability Management – Vulnerability Scanning, Assessment along with real-life pen-testing solution. SecPoint is Number 1 top rated Network Security Vulnerability Scanner, Assessment & Penetration testing solution.
Key Features
- No experience necessary to operate. User friendly to Setup.
- Performs vulnerability scanning of your public website and IPs along with your internal local IPs.
- 64 Bit Vulnerability Scanner High Power Support.
- No backdoors in product – All information at customer site – No data gathering
- Includes both the SecPoint vulnerability scanner and penetration tester Vulnerability Scanning Capabilities.
- Penetrator has an IP address. So you just need to login to the web interface and configure the IP address. You can set it on the Internal or External network and reach the Penetrator administration interface from the Internet.
- Secure your network with the best Vulnerability Scanner.
- Penetration Testing – Pentesting – Vulnerability Scanner
- Vulnerability Assessment Joomla Security Checker, Joomla Vulnerability Scan.
- Advanced Vulnerability Scanning Profiles: Normal Scan, OWASP Scan, Firewall Scan, SEO Black Hat DB Scan, Extended Scan, SANS Scan, Aggressive Scan.
- It comes fully loaded with Automated functionality. CVE, Bugtraq, OVSDB compliance reporting. Easy to use scanning profiles for Normal scan, Web Scan, OWASP scan, Aggressive Scan, Firewall Scan, Extended Firewall Scan


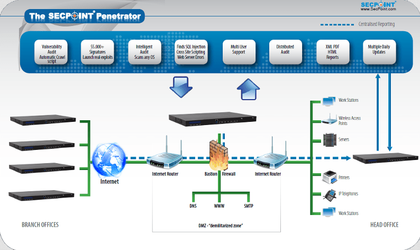



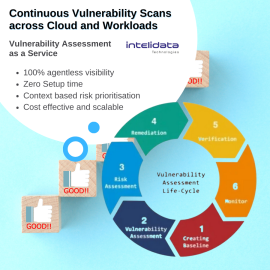


Description
SecPoint is a Danish IT security company which has developed security solutions, each ahead of it’s competitors in their markets:
The Protector has features such as High Speed Firewall and UTM capability. Best Anti Spam, Multi Engine Anti-Virus, Web Filter, HIgh Speed IPS multi core Engine.
The Penetrator has features such as Vulnerability Management, Security Assessment, Penetration Testing, Audit any OS, Distributed Audit, Launch Real Exploits, Launch Real DoS Attacks, Reports Branding and comes in Portable and fully standalone appliance versions.
The Portable Penetrator has features such as Wireless WiFi security auditing of open networks, WEP, WPA and WPA2 Protected networks. Further more it also incorporates the other features of the Penetrator such as Vulnerability Management, Security Assessment, Penetration Testing, Audit any OS, Distributed Audit, Launch Real Exploits, Launch Real DoS Attacks.