Description
Secure Code Review
Secure Code Review is a process which identifies the insecure piece of code which may cause a potential vulnerability in a later stage of the software development process, ultimately leading to an insecure application. When a vulnerability is detected in earlier stages of SDLC, it has less impact than the later stages of SDLC – when the insecure code moves to the production environment.
The secure code review process comes under the Development Phase, which means that when the application is being coded by the developers, a security analyst can perform the code review, as the security experts have a more intrinsic view of security issues. Different studies and surveys shows that approximately 75% of attacks happen due to an insecure application, inside which includes insecure code. This way, it becomes a very essential part of SDLC which should be performed rigorously.
Secure Code Review is performed in accordance with Open Web Application Security Project (OWASP) industry best practice guidelines. At minimum, security assessment must include OWASP Top 10 security risk.
Intelidata Team Approach
Define scope: Understand the business logic of the application, which vulnerabilities you need to look for, such as OWASP Top 10, SANS, etc…Then deduce how many of them can be detected using tools and which are best suited for manual review.
Categorize the vulnerabilities: What is your priority, meaning what type of vulnerabilities you will take as a priority? For example, in business applications, you may concentrate mostly on the business logic of the application and dive deep into it, as the technical ones are easily detected by tools. Prioritize them.
The following are a few categories you can look at:
- Authorization
- Authentication
- Injection flaws
- Improper error handling/Exception flaws
- Encryption (Cryptography)
- Auditing and Logging
- Session related flaws (Session management)
Recommendation: As a security analyst, it’s our duty to filter false positives generated by tools and validate them in order to confirm that they are actual flaws. After doing a proper code review, you should document the vulnerabilities found in a comprehensive report coating the category of the vulnerability and their mitigation.
Talk to developers first: The more you involve developers in your code review process, the more effective the analysis will be. You get confidence that whatever you are doing is based on the right understanding of the code.
Methodologies used for secure code review:
- Automated scanning of source code with open source/commercial tools.
- Manual review of the code for identification of security design issues by asking your developers a comprehensive list of security questions.
- Analyze the areas in the application code which handle functions regarding authentication, session management and data validation.
- Identification of un-validated data vulnerabilities contained in your code.
- Identification of poor coding techniques allowing attackers to exploit them for launching targeted attacks.
- Evaluation of security issues specific to individual framework technologies.
Techniques to secure code review:
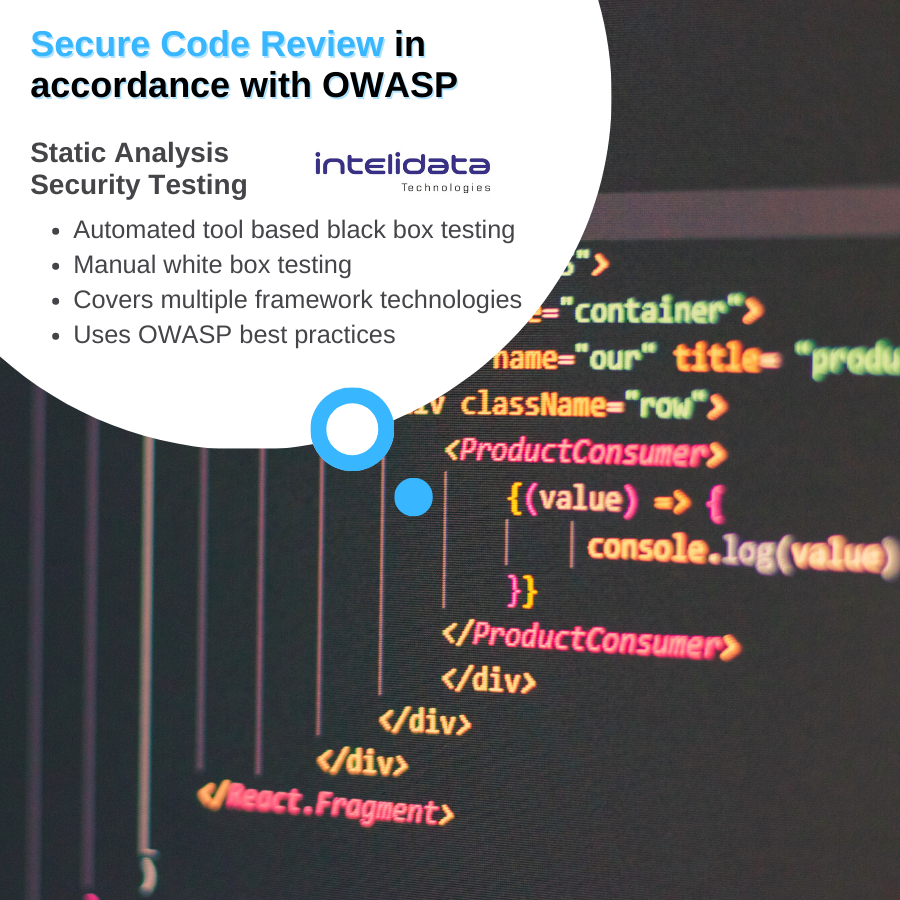
- Automated tool based/ Black Box: In this approach, the secure code review is done using different open source/commercial tools.
- Manual/ White Box: The automatic tool scanner flags the whole code with vulnerabilities based on its perception. Thus a manual / white box testing is required .In this technique, a thorough code review is performed over the whole code, which may become a very tedious and tiresome process. But in this process, logical flaws may be identified which may not be possible using automated tools, such as business logic problems. Automated tools are mostly capable of finding technical flaws such as injection attacks.





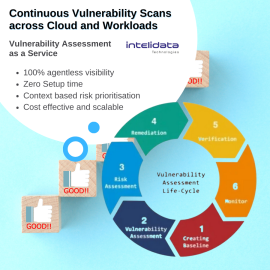






Description
Technical Experience
We are a qualified & highly technical team of Experienced Cyber Security Researchers, with cumulative experience of 25+ years. We partner with small to mid-sized companies to secure their businesses with easy step-by-step proven processes & Cert-in guidelines.
24/7 Services
We offer round-the-clock technical assistance. We never turn the cell phone off. It’s on 24/7 and it gets answered whenever you call, to give you timely deliveries. By outsourcing your IT security to us, you can focus on what you do best–running your business.
Flexible Pricing
No unexpected bills. No budget blow-outs. No missed deadlines. No broken promises. No shoddy service. No surprises. We believe in adding value to your business and provide meaningful service at a very cost efficient and budget -friendly pricing.
Training Assistance
We provide detailed steps & Cyber Security training to your Web Administrators and Developers for patching. No matter the budget, we pride ourselves on providing comprehensive professional assistance to them to secure your business.