Description
Cyber Attacks have become sophisticated than ever before. Organizations are challenged with proactively detecting the attacks, respond and timely mitigation. Typically Organizations deploy Security platforms like firewalls, Intrusion Detection / Preventions etc. However, attackers use new techniques and hide the attack below normal protocol and operations. Not only that, they dynamically keep changing the attack landscape and attack delivery methods.
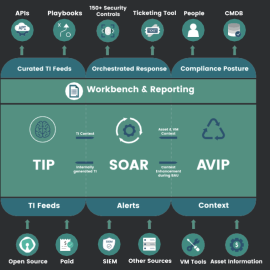
In this advance Technical exercise, we will use Threat intelligence and SIEM (Security Information and Event Management technologies to detect variety of threats.












Description
We are a niche cyber security company established by highly motivated technologists. We offer unparalleled security consulting, auditing and security as a service. We help you organization by offering security solutions and advisory services to identify, control and eliminate security threat to your information technology assets. When it is the matter of trust and securing your organization, you can count on our expertise.
strategy formulation, technology implementation, process orientation, governance risk compliance, privacy protection systems, threat and vulnerability analysis, penetration testing, security education and training