Description
Privileged Access Management (PAM) is one of the most important areas in Information Security. As the term suggests, privileged access is granted to privileged users. The privileged users have elevated access rights to business-critical applications, databases, cloud-resources, DevOps, CI/CDs environments among other highly sensitive data-assets.
Thus, managing, monitoring and controlling the privileged access is extremely important. Misuse or abuse of trusted privileges is one of the biggest sources of data breaches and abuse of sensitive information.
A robust privileged access management is essential to thwart insider threats, third-party risks and advanced cyber-attacks. Privileged Access Management practice helps to ensure that any unauthorized access to target systems is denied.
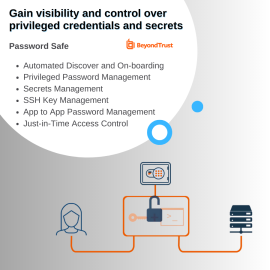
Besides, Privileged Access Management is essential from the compliance perspective. A host of IT standards such as PCI-DSS, HIPAA, ISO 27001, and regulations (GDPR) among many other local regulations as mandated by governments and central banks explicitly ask for role and rule-based access, Multi-factor authentication (MFA), password vaulting, etc. to protect data. The solution offers all the necessary safeguards.
However, the level of complexities in managing privileged users is increasing; so is the level of the privileged access control. Many global organizations have distributed datacentre environments. More and more organizations are adopting cloud-computing. IT developers have privileges to access DevOps tool chains. Furthermore, the pandemic and its implications have meant that most of the workforce access systems remotely.
All these use-cases have necessitated granular control over privileged users along with a strong validation mechanism. Against this backdrop and the proliferation of privileged users, a robust Privileged Access Management is a must to ensure authorized and controlled access to systems.






Description