Description
We help Enterprises to identify, prevent, detect, resolve, and protect their critical data from threats, crimes, frauds, and acts of terrorism arising due to vast proliferation and usage of Digital, Communication applications and artifacts in their personal and professional lives. We also provide assistance for legal enforcement to customer.
We also provide the 65B Certificate which is an important aspect to prove an innocent/guilty in the court of law.
Services under Cyber Forensic Investigation
- Computer Forensics
- Network Forensics
- Mobile Devices Forensics
- Data Breach
- Digital Image Forensics
- Digital Video/Audio Forensics
- Memory Forensics
- Harassment via e-mails
- Financial frauds and crimes
- Cheating and Fraud
- Compromised Customer data
- Possession of unauthorized information
- Distribution of Pirated Software
- Unauthorized disclosure of internal and confidential information
What has to be done for a successful Cyber Forensic Investigation?
Cyber forensic investigation is a very sensitive procedure which requires only skilled person to conduct the investigation. Our team of skilled professionals perform cyber forensic investigation in forensically sound conditions.
Process of Cyber forensic Investigation includes but not limited to: –
1) Identify the crime
This is the information gathering stage where information about the crime happened is gathered.
Identifying the type of cybercrime helps the investigator to perform investigation more crucially and collect the required software’s/hardware for investigation.
2) Imaging/Cloning
If the identified cybercrime involves the use of Computers, PC’s or Mobile Devices then the process of Imaging/Cloning is performed wherein a Forensic Image is obtained. A forensic image (forensic copy) is a bit-by-bit, sector-by-sector direct copy of a physical storage device, including all files, folders and unallocated, free and slack space. Forensic images include not only all the files visible to the operating system but also deleted files and pieces of files left in the slack and free space.
3) Analysis
This steps formally includes the analysis of all artifacts with the help of forensic software’s.
4) Forensic Report
After completion of analysis, a detailed investigation report is provided having all findings, observation, conclusion and POC





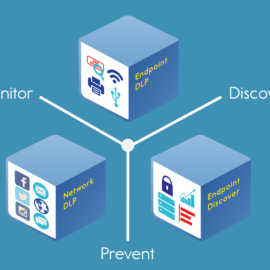
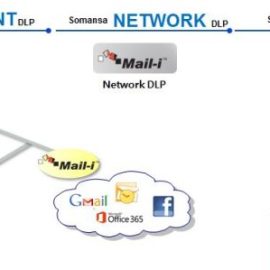
Description
Technical Experience
We are a qualified & highly technical team of Experienced Cyber Security Researchers, with cumulative experience of 25+ years. We partner with small to mid-sized companies to secure their businesses with easy step-by-step proven processes & Cert-in guidelines.
24/7 Services
We offer round-the-clock technical assistance. We never turn the cell phone off. It’s on 24/7 and it gets answered whenever you call, to give you timely deliveries. By outsourcing your IT security to us, you can focus on what you do best–running your business.
Flexible Pricing
No unexpected bills. No budget blow-outs. No missed deadlines. No broken promises. No shoddy service. No surprises. We believe in adding value to your business and provide meaningful service at a very cost efficient and budget -friendly pricing.
Training Assistance
We provide detailed steps & Cyber Security training to your Web Administrators and Developers for patching. No matter the budget, we pride ourselves on providing comprehensive professional assistance to them to secure your business.